RapidFire Tools Updates
Compliance Manager GRC Updates
The New Compliance Manager GRC NIST CSF 2.0 Standard
The National Institute of Standards and Technology (NIST) has recently released the NIST Cybersecurity Framework (CSF) 2.0, a revised version of the framework designed to help all organizations manage and reduce risks. To help organizations navigate the changes to the NIST CSF, Compliance Manager GRC now includes a new NIST CSF 2.0 standard.
What’s Changing With NIST CSF 2.0?
In NIST’s announcement of NIST CSF 2.0 on February 26, 2024, NIST stated that:
- The new NIST CSF 2.0 IT security framework now explicitly aims to help all organizations, not just those in critical infrastructure, its original target audience, to manage and reduce risks.
- NIST updated the CSF’s core guidance and created a suite of resources to help all organizations achieve their cybersecurity goals, with added emphasis on governance and supply chains. This guidance includes:
- NIST CSF 2.0 Informative References that point to sources of guidance on each outcome from existing global standards, guidelines, frameworks, regulations and policies, including references to a catalog of tools (called controls) for achieving specific cybersecurity outcomes, including the Center for Internet (CIS) Critical Security Controls, the Cyber Risk Institute (CRI) Profile controls and SP 800-53 Rev. 5 controls.
- NIST CSF 2.0 Implementation Examples that illustrate potential ways to achieve each outcome desired by the NIST CSF 2.0 subcategory (requirement).
Adapting to Change With Compliance Manager GRC
The new NIST CSF 2.0 Standard is now available for use within Compliance Manager GRC to enable organizations to assess and manage ongoing compliance with the NIST CSF 2.0 security requirements implemented to secure their business IT systems comply with regulatory requirements. The new Compliance Manager GRC NIST CSF 2.0 Standard includes:
- NIST CSF 2.0-specific “Guidance” referring to the NIST-specified NIST CSF 2.0 Informative References and Implementation Examples.
- NIST CSF 2.0 security requirements mapped to the CIS Controls and the CRI Profile v2.0 controls specified in the NIST Informative References for reference and use during the requirements and controls assessment process used to assess an organization’s current compliance with the NIST CSF 2.0 requirements and to manage continuous compliance needs.
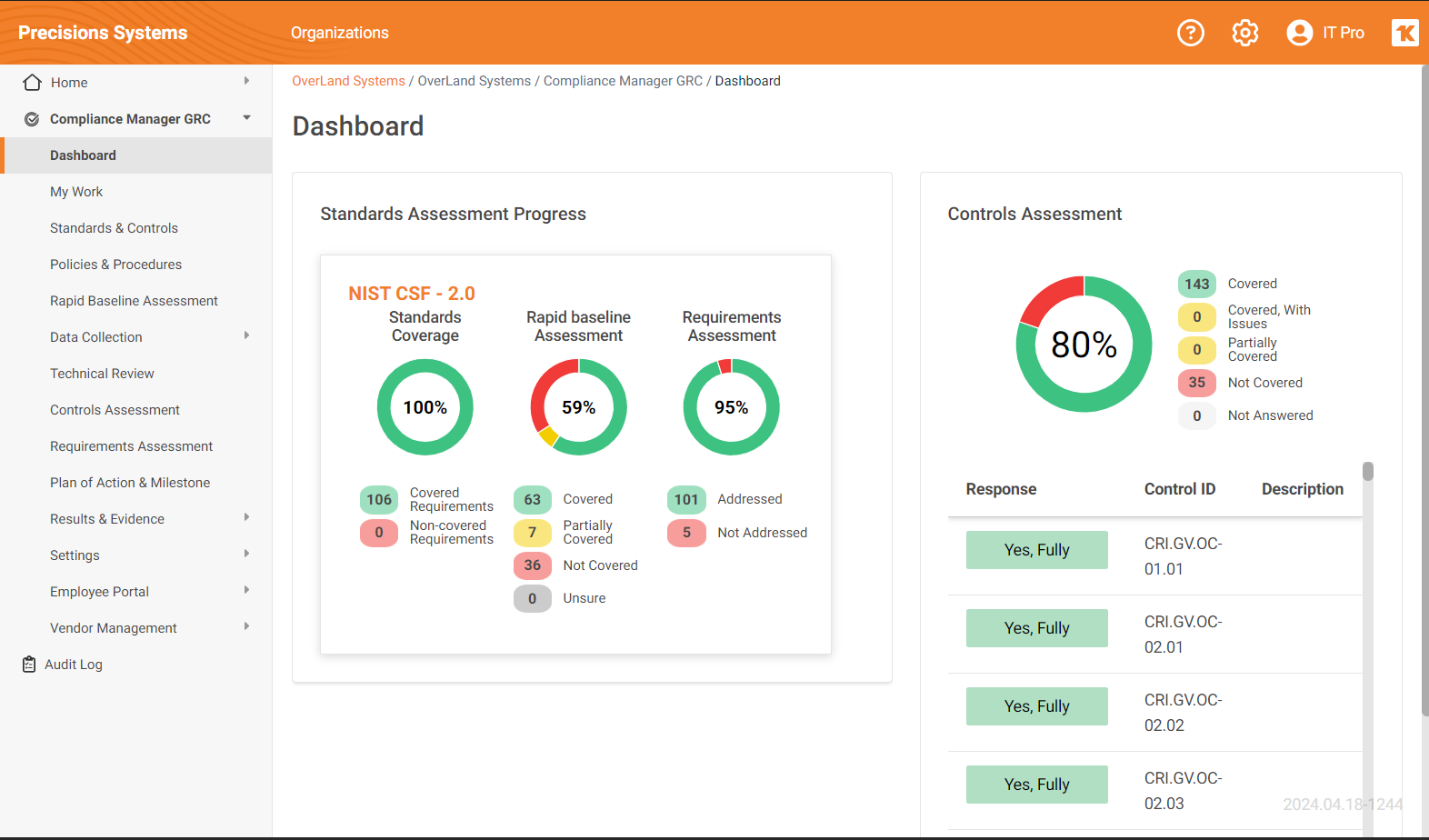
With features like Compliance Assessments, Technical Risk Assessments, Compliance Status Dashboards and Reporting, and Employee and Vendor Risk Management, Compliance Manager GRC simplifies the process of achieving and maintaining compliance.
Why This Matters
The new NIST CSF 2.0 IT security framework reflects NIST’s efforts to enhance cyber governance, mitigate risks, and protect businesses and consumers. In this context, Compliance Manager GRC serves as more than just a tool. It’s a partner in ensuring your organization is compliant, secure and prepared for the dynamic world of cybersecurity governance.
Act Now!
With the enhanced capabilities of Compliance Manager GRC, managing compliance with the NIST CSF 2.0 standard is more straightforward and efficient. Visit our website to explore how Compliance Manager GRC can revolutionize your compliance journey or contact us for a detailed demonstration. Don’t let regulatory changes slow you down. Stay compliant, secure and ahead in the ever-changing landscape of cybersecurity governance with Compliance Manager GRC.
Compliance Manager GRC’s NYDFS Part 500 Updates
The world of compliance is constantly evolving, and staying ahead of these changes is crucial for businesses, especially in the financial sector. The New York State Department of Financial Services (NYDFS) has recently updated its Part 500 23 NYCRR standards, a move that significantly impacts entities operating under its regulations. To help organizations navigate these changes, Compliance Manager GRC has introduced three new standard variants, each tailored to different types of covered entities.
What’s Changing with NYDFS Part 500?
These updates represent a substantial shift in the requirements for cybersecurity governance and risk management. Key changes include the introduction of a new category for large (“Class A”) companies, enhanced governance requirements, stricter board oversight and certification processes, comprehensive technical requirements for all covered entities, and new policies and risk assessment cadences. Additionally, business continuity and disaster recovery requirements have been updated to reflect the growing need for resilience in the face of cybersecurity threats.
Adapting to Change with Compliance Manager GRC
To assist covered entities in adapting to these evolving standards, Compliance Manager GRC has been updated with three new NYS DFS Part 500 23 NYCRR Standard Variants. These include:
- Large (“Class A”) Companies
- Non-Class A, Non-Exempt (“Standard”) Companies
- Small (“Exempt”) Companies
These variants offer comprehensive standard management, allowing users to align their IT security tools and systems with the NYDFS Cybersecurity Regulation requirements. With features like Rapid Baseline Assessments, Technical Risk Assessments, Documentation and Reporting, and Employee and Vendor Risk Management, Compliance Manager GRC simplifies the process of achieving and maintaining compliance.
Why This Matters
The updated regulations reflect NYDFS’s efforts to enhance cyber governance, mitigate risks, and protect businesses and consumers. In this context, Compliance Manager GRC serves as more than just a tool; it’s a partner in ensuring your organization is compliant, secure, and prepared for the dynamic world of cybersecurity governance.
Act Now
With the enhanced capabilities of Compliance Manager GRC, managing compliance with the updated NYDFS Part 500 standards is more straightforward and efficient. Visit our website to explore how Compliance Manager GRC can revolutionize your compliance journey or contact us for a detailed demonstration. Don’t let regulatory changes slow you down - with Compliance Manager GRC, stay compliant, secure, and ahead in the ever-changing landscape of cybersecurity governance.
Compliance Manager GRC Updates
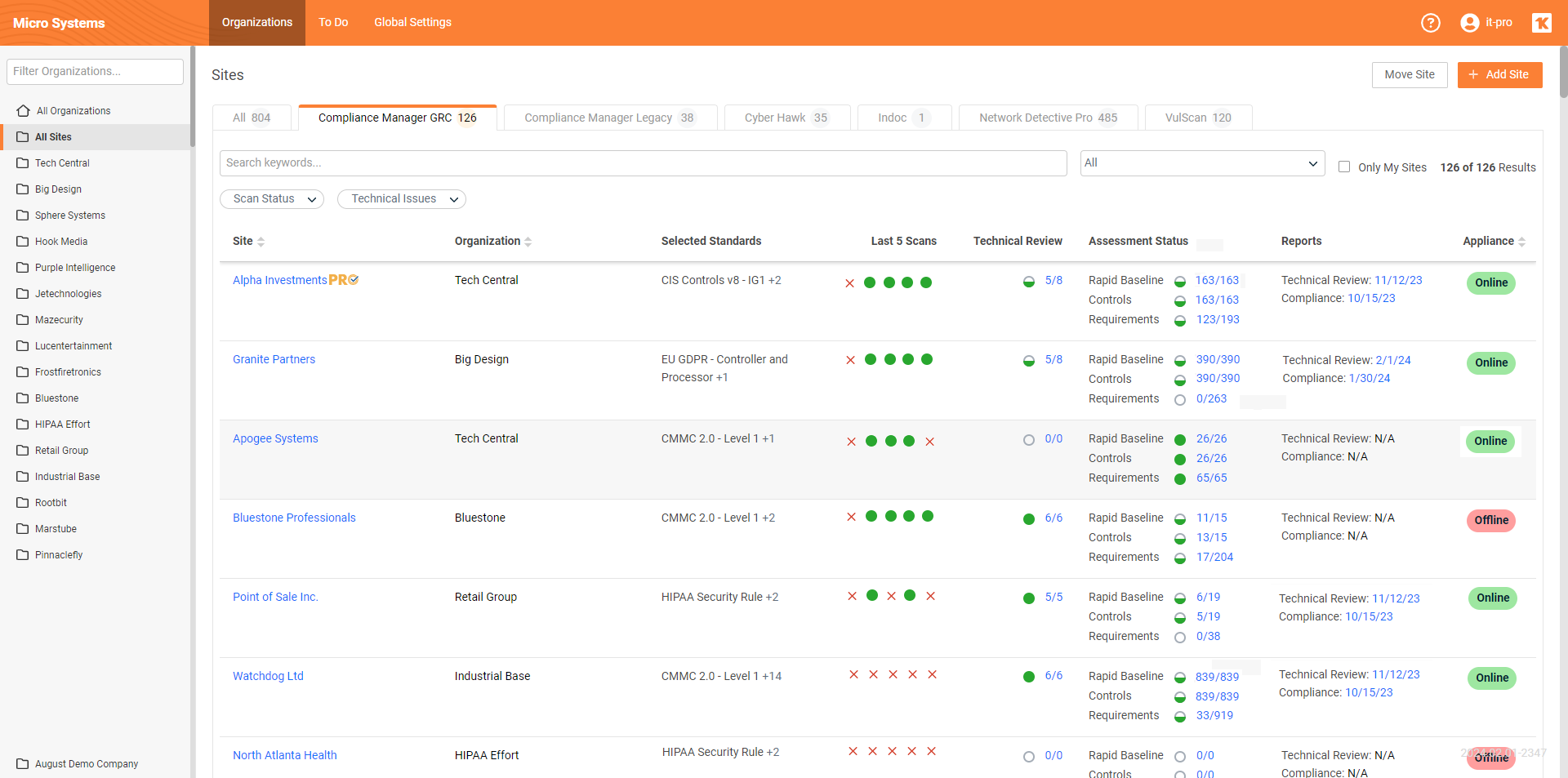
Introducing Multi-sites View for MSP and SMB IT Admins
We have unveiled the latest feature to enhance your experience with Compliance Manager GRC. “Multi-sites View for MSP and SMB IT Admins”. This new feature is designed to radically streamline your workflow and increase efficiency in managing multiple Compliance Manager GRC sites.
The Multi-sites View offers a centralized, comprehensive overview of all your Compliance Manager GRC Sites in a single, easily navigable portal page. This ‘Single Pane of Glass’ approach simplifies how you manage and perform technical reviews and compliance assessments across multiple sites.
Key Features and Functionality:
Enhanced User Interface: Introducing the new YourIT Portal Sites Page and Compliance Manager GRC Sites List View Page, offering intuitive navigation and interaction.
Efficient Site Management: Quickly view the status of site scan data collection, technical reviews, compliance assessments, and report generation.
Advanced Interaction Capabilities: Interact with the site list to view and select site names, organization names, and access detailed site information.
Comprehensive Status Overview: Monitor the status of site scans, technical review assessments, compliance assessments, report generation, and server appliance status.
Customizable Site List View Filters: Tailor the site list view based on criteria like ‘My Sites’, ‘Scan Status’, and ‘Technical Issues’, enhancing focus and efficiency.
Previously, managing several dozens, or even hundreds of Compliance Manager Sites meant opening and reviewing each site individually. The Multi-sites View addresses this by allowing users to quickly assess the status of each site’s key components, making the process of deciding and performing next actions more efficient.
Professionals that are responsible for IT Security Frameworks and Regulatory Compliance assessments will find their productivity significantly enhanced with this feature.
As we continue to innovate and refine our tools, we remain committed to providing top-tier security and compliance solutions for MSPs. Stay tuned for more updates, features, and integrations!
Compliance Manager GRC Updates
Streamline your compliance processes with new Evidence of Compliance Intergrations
We are thrilled to announce the release of our new set of ‘Evidence of Compliance’ integrations for Compliance Manager GRC. They significantly reduce the time and effort required in conducting compliance assessments, a key benefit in today’s fast-paced business environment. Furthermore, they automate the collection and mapping of crucial compliance data, which is essential for maintaining accuracy and consistency in compliance reporting.
These integrations, as part of our IT Complete strategy, are meticulously designed to simplify the compliance processes for our users, delivering an enhanced security and compliance posture. IT Complete, as a part of Kaseya’s broader vision, continually evolves with new features and integrations, harnessing the power of automation, machine learning, and artificial intelligence to streamline IT management tasks and provide a unified solution for backup, security, compliance, and disaster recovery.
Below you will find a detailed look into each integration.
RocketCyber Endpoint, Firewall, and Microsoft 365 Evidence of Compliance - Automates threat monitoring by integrating key security metrics into compliance frameworks and automatically mapping the corresponding evidence to endpoint, firewall, and Microsoft 365 compliance controls, while importing relevant data into Compliance Manager GRC.
Dark Web ID Monitored Domains Evidence of Compliance - Enhances domain security by targeting dark web monitoring, automatically mapping evidence files to compliance controls, and importing domain security assessment data into Compliance Manager GRC.
BullPhish ID Security Training Evidence of Compliance - Bolsters security protocols education by integrating and automatically mapping key security awareness training metrics to relevant compliance controls, alongside importing this data into Compliance Manager GRC.
Datto BCDR Endpoint Backup Evidence of Compliance - Facilitates compliance evidence compilation for endpoint backups by integrating backup data from Datto BCDR, mapping this evidence automatically to compliance controls, and importing data into Compliance Manager GRC.
Datto EBS Direct-to-Cloud Server Backup Evidence of Compliance - Streamlines server backup compliance by facilitating data protection strategies, automatically mapping backup evidence to compliance controls, and importing data into Compliance Manager GRC.
Datto RMM Patch Management Evidence of Compliance - Simplifies software patch management and compliance by aligning with requirements, automatically mapping patch management evidence to compliance controls, and importing relevant data into Compliance Manager GRC.
Passly Two Factor Authentication Evidence of Compliance - Enhances organizational security by incorporating two-factor authentication data, automatically mapping this evidence to compliance controls, and importing data into Compliance Manager GRC.
Datto EBPC Direct-to-Cloud PC Backup Training Evidence of Compliance - Streamlines compiling compliance evidence for PC backups by automating integration of PC backup metrics from Datto EBPC, mapping this evidence to compliance controls, and importing data into Compliance Manager GRC.
Graphus Cloud Email Security Training Evidence of Compliance - Strengthens defenses against phishing by integrating email security training metrics, automatically mapping this evidence to compliance controls, and importing data into Compliance Manager GRC.
Datto EDR Endpoint Threat Detection and Response Evidence of Compliance - Enhances security posture by automating the incorporation of endpoint threat detection and response metrics, mapping this evidence to compliance controls, and importing data into Compliance Manager GRC.
Datto Backup for Microsoft Azure Cloud VM Backup Evidence of Compliance - Streamlines backup compliance for cloud VMs by automating the injection of backup metrics from Datto Backup for Microsoft Azure, mapping this evidence to compliance controls, and importing data into Compliance Manager GRC.
Each of these integrations is specifically designed to reduce the workload for Compliance Manager GRC users, focusing on efficient data collection and streamlined compliance audits. Stay tuned as we continue to evolve our compliance management solutions, always aiming to provide top-notch security and compliance tools.
VulScan Updates
Elevate Your Cybersecurity with VulScan’s Known Vulnerabilities Flag Feature
VulScan now offers a cutting-edge Known Vulnerabilities Flag feature, enhancing your ability to identify and prioritize critical security threats. This new functionality integrates seamlessly into VulScan’s robust vulnerability management system, offering unparalleled protection and insight.
Instantly Identify Critical Threats
The Known Vulnerabilities Flag feature is designed to immediately highlight vulnerabilities that are actively exploited in the wild, as listed in CISA’s Catalog of Known Exploited Vulnerabilities. This prioritizes remediation efforts, focusing on the most critical issues first.
Seamless Integration in Reports and Dashboards
Known Exploited Vulnerabilities are now labeled across all aspects of VulScan, including scan results, export reports, and notifications. This integration ensures you’re always informed about the most critical vulnerabilities in your network.
Tailored Notifications and Export Options
Customize your alert settings to receive notifications specifically for detected Known Exploited Vulnerabilities. Export these critical vulnerabilities separately to your preferred PSA system, ensuring focused and effective remediation strategies.
Comprehensive Dashboard View
A dedicated section on the VulScan Dashboard now displays a list of all Known Exploited Vulnerabilities detected in your scans. This feature allows for quick assessment and prioritization of these critical threats.
By incorporating the Known Vulnerabilities Flag feature, VulScan continues to lead in providing comprehensive, easy-to-use vulnerability management solutions, ensuring your networks are protected against the most pressing cyber threats.
For more details, visit the VulScan product page.

VulScan Updates
Elevate Your Scanning with VulScan’s Hostname Scanning Feature
In our continuous quest to enhance VulScan’s capabilities, we’re introducing a new feature: Hostname Scanning for both Internal and External Vulnerability Scans. This new feature expands our scanning arsenal beyond the conventional IP address scanning, enabling scans via hostnames and domain names. This significant enhancement facilitates a more focused and precise approach to identifying and addressing vulnerabilities, ensuring a robust and comprehensive security posture for organizations.
This new development in VulScan’s suite of tools is a testament to our dedication to continually evolving and improving our cybersecurity solutions to meet the dynamic needs of today’s digital landscape and includes the following functionality.
Flexible Scanning Methods - Perform internal scans using hostnames and external scans using domain names, along with traditional IP address scanning. This enables precise targeting of specific network segments or devices, improving the accuracy of vulnerability assessments.
Dynamic IP Address Solution - Ideal for environments where IP addresses frequently change, ensuring continuous and comprehensive monitoring. This feature also automates the tracking of changing IP addresses, ensuring no device is missed during security assessments.
Simplified Process - Hostname and domain name scanning provides a more user-friendly alternative to IP address scanning, especially in complex network setups. The feature decreases the learning curve for new users, facilitating quicker adoption and integration into existing workflows.
Comprehensive Network Coverage - Combine hostname/domain name scanning with IP address scanning for a thorough network vulnerability assessment. The feature delivers a holistic view of the network’s security posture, identifying vulnerabilities that may be overlooked by single-method scans.
Dynamic IP Address Challenge - Given the prevalence of dynamic IP addresses, it’s essential to maintain consistent coverage without constant manual adjustments to scan settings. This provides uninterrupted security surveillance, crucial for networks with frequent IP address changes.
Reduced Manual Effort - This feature significantly cuts down the time and effort required to keep dynamically changing IP addresses under constant surveillance. Optimizing resource allocation and increased operational efficiency allows IT staff to focus on other critical aspects of cybersecurity.
Enhanced Security - Simplified scanning of all devices bolsters your organization’s overall security posture. Comprehensive coverage of all networked devices strengthens security defenses.

Compliance Manager GRC Updates
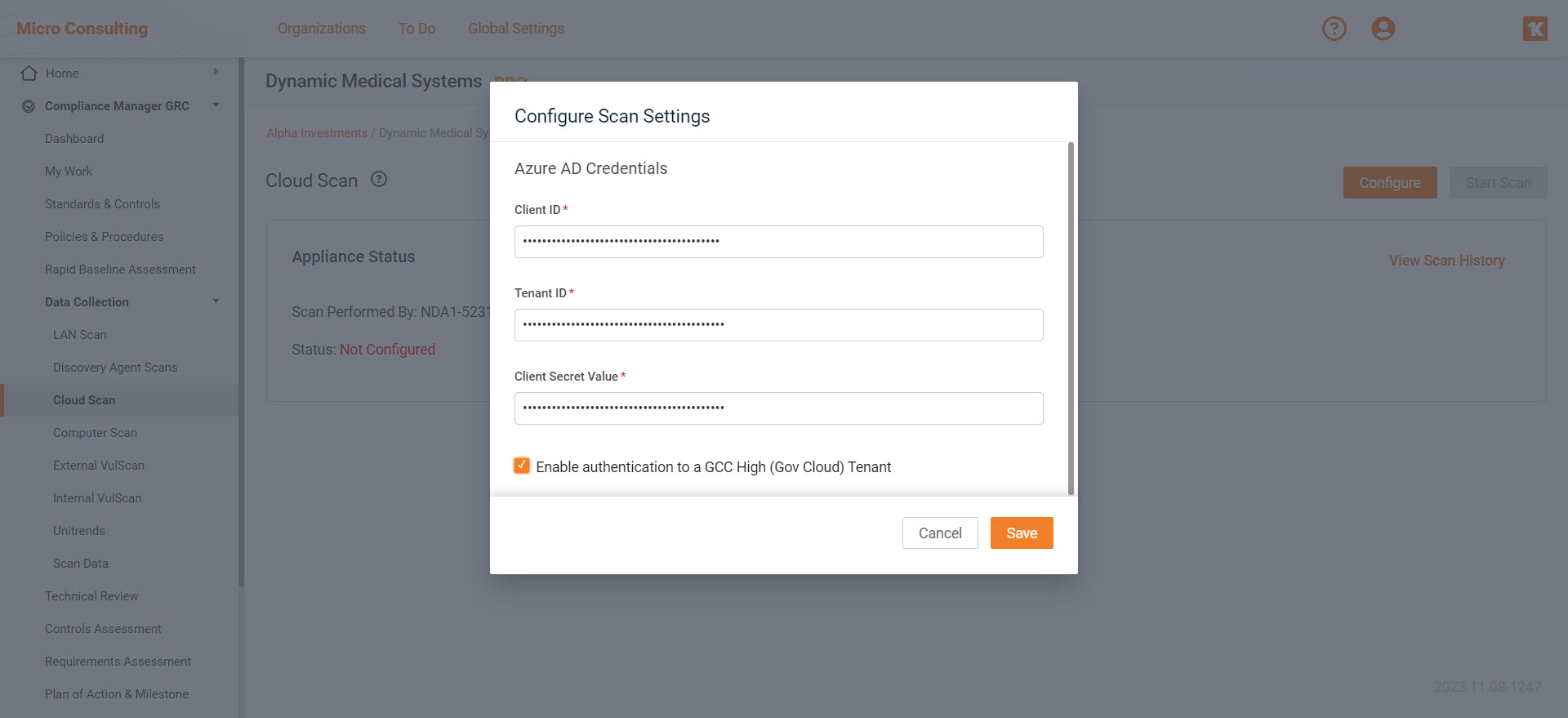
Revolutionizing Compliance in the Microsoft US Government Cloud with the GCC High Azure AD Scan
The introduction of the GCC High Azure AD Scan within Compliance Manager GRC marks a advancement in compliance technology for the Microsoft US Government Cloud. GCC High, or Government Community Cloud High, is a dedicated environment in Microsoft Azure tailored for U.S. federal, state, local, and tribal governments, as well as contractors managing sensitive data like CUI and ITAR data. This Compliance Manager GRC feature is precisely engineered to meet the rigorous compliance and security standards required in this specialized cloud environment. By enabling access to and scanning of Azure Active Directory (AD) within GCC High, the tool ensures dynamic adaptability to changing Azure Tenant settings and evolving compliance requirements, making it an essential asset for maintaining up-to-date and responsive compliance postures.
The GCC High Azure AD Scan is also designed with user accessibility in mind. Its integration into Compliance Manager GRC includes a user-friendly interface, simplifying the process of configuring and activating scans in the GCC High environment. A key feature is the “Enable authentication to a GCC High (Gov Cloud) Tenant” setting, facilitating seamless interaction with Azure Tenants. For organizations tasked with adhering to stringent government standards, this tool not only enhances compliance management but also provides the ability to adapt to the ever-evolving landscape of IT security and regulatory compliance in the government sector.
Network Detective Pro Online
Introducing Network Detective Pro Online, A web-based platform for IT Assessments
We have launched Network Detective Pro Online, an upgrade to the existing Network Detective Pro platform. This new web-based platform is designed to transform the way MSPs, and network administrators conduct IT assessments, bringing a suite of advanced tools and features to your fingertips.
Network Detective Pro Online is not just an update; it’s a complete reimagining of IT assessments. It’s designed to elevate your service offerings, enhance your operational efficiency, and provide comprehensive insights into the networks you manage.
It includes the following features:
Real-Time Data and Analytics - Network Detective Pro Online offers real-time monitoring and data collection, ensuring that the information is always current and actionable. This shift to live data enhances the accuracy and relevance of network assessments.
Enhanced User Interface and Experience - Network Detective Pro Online boasts a modern, intuitive interface that simplifies navigation and enhances user engagement. The new design is tailored to be more user-friendly, making it easier to access and interpret complex data.
Comprehensive Reporting - Network Detective Pro Online takes reporting a step further by offering over 100 customizable report types, including executive summaries and detailed technical reports. These reports are now more adaptable to varying business needs and can be branded for a professional touch.
Integration and Automation - Network Detective Pro Online features seamless integration with a wide range of tools like IT Glue, PSAs, and VulScan. The platform also automates several processes, such as the deployment of data collectors and report generation, streamlining workflow and saving valuable time.
Scalability and Adaptability - Network Detective Pro Online is designed to effortlessly scale and adapt to various IT environments, including on-premises, cloud-based, and hybrid systems. This makes it a more versatile tool for businesses of all sizes.
Continuous Improvement and Updates - Network Detective Pro Online, not only continues with regular updates but also introduces a dynamic approach to feature enhancements, ensuring that the platform remains at the forefront of IT assessment technology.
As a fully web-based platform, Network Detective Pro Online allows its users to access and manage network assessments from anywhere, at any time. This change enhances flexibility and convenience, particularly for remote or on-the-go assessments.
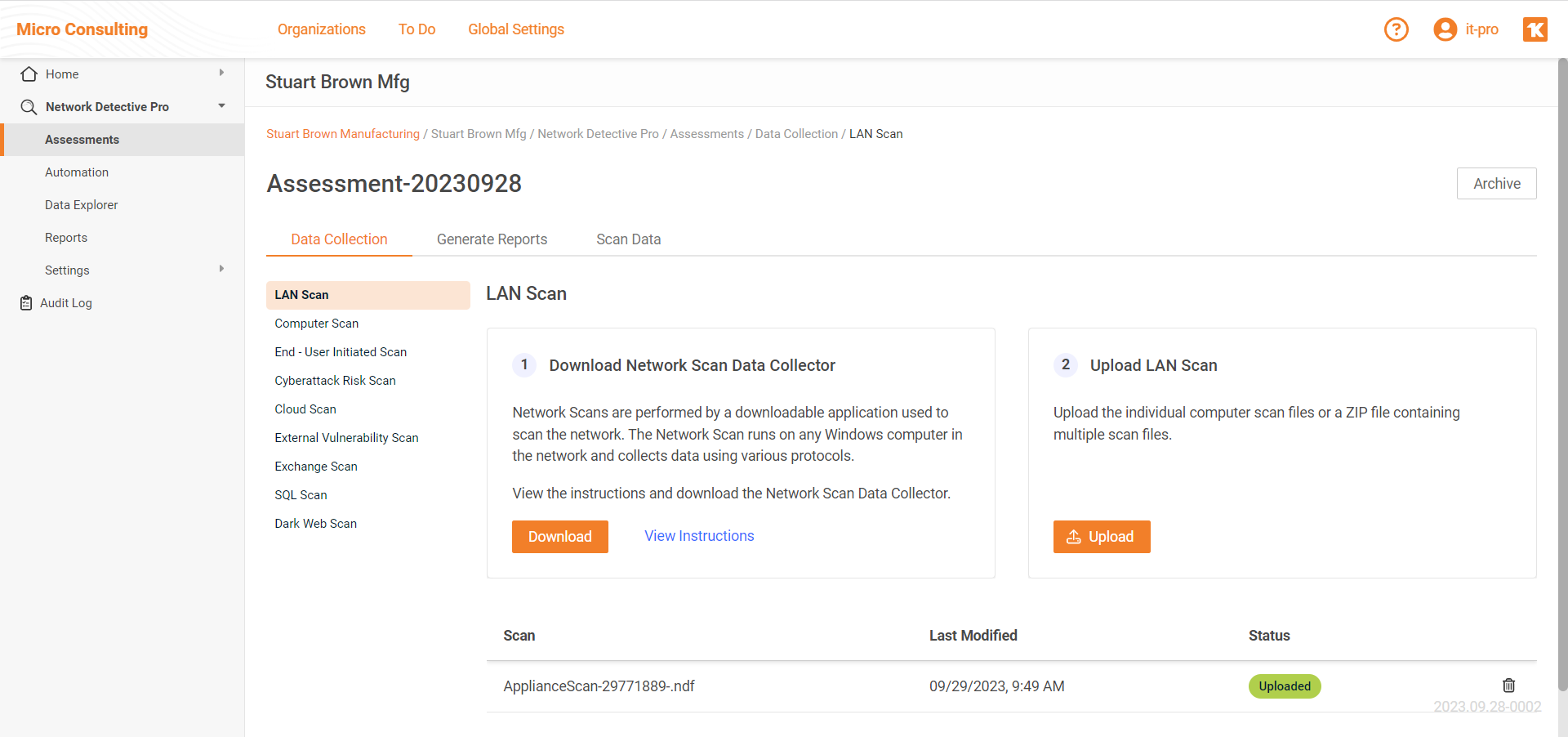
VulScan Updates
New Hosted External Vulnerability Scanning
If you lack the resources to set up your own external vulnerability scanning environment – or just want to rid yourself of the cost and hassles associated with managing and maintaining an external data center for this purporse – our Hosted External Vulnerability Scanner service is here to help.
Available as a low-cost add-on subscription exclusively for VulScan users, this new service is fully-integrated into the VulScan user-interface, and uses the exact same workflow as if you were hosting the scanners yourself, but without the complexity of deploying and setting up any scanning appliances.
Subscribers for this service simply select the hosted scanning option from inside the VulScan user interface, input the external IPs they want to scan, set the desired scan frequency, date and time. The scans are automatically performed by devices within our controlled server farm environment, ensuring high performance and availability. Upon completion of the scans, the results are immediately sent back to the VulScan dashboard, combined with any internal vulnerability scan results performed on the same site.
The monthly subscription for this add-on service is based on the number of external IP addresses you need to scan, and the frequency of the scans. The low monthly subscription fee includes 100 scans – which means you can scan 100 external IP addrsses per month, or 50 external IP addresses every two weeks, or 25 external address every week, or any other combination totalling 100 scans per month. If you need to scan additional IP addresses or scan them more frequently, you can add more at any time.

VulScan Updates
Revolutionizing Security with VulScan’s - Application Vulnerability Scanning
VulScan’s Vulnerability Discovery Agents have been enhanced to detect vulnerabilities in more than 200 of the most common software applications that run on Windows computers. These agents previously just scanned the Windows Operating System and selected Microsoft software applications.
Application scanning is an important feature of network vulnerability scanning because it specifically focuses on identifying vulnerabilities and weaknesses within the software and applications running on networked devices. This is crucial for several reasons:
- Comprehensive Security Assessment
- Patch Management
- Customized Exploits
- Data Protection
- Regulatory Compliance
- Security Posture Improvement
- Incident Response
This new feature leverages our Discovery Agents to:
- Automatically identify unpatched third-party applications with security vulnerabilities.
- Provide insights into the latest application versions containing critical fixes.
- Seamlessly integrate vulnerabilities into Scan Results, Dashboards, and VulScan Reports.
- Enable export to PSA systems and trigger email notifications alongside other security alerts.

VulScan Updates
Unlock Your Network’s Secrets with the VulScan Open Ports Report
The VulScan Open Ports Report is a comprehensive documentation of open ports on various devices such as computers, servers, and routers. It is initiated with both internal and external vulnerability scans performed by any VulScan appliance. It determines whether ports are open or closed, and reports back a list of devices, the port number and services utilizing them.
This reporting feature allows you to review the results in the VulScan portal, filter the data on any field, and optionally export the results in Excel format.

Compliance Manager GRC Updates
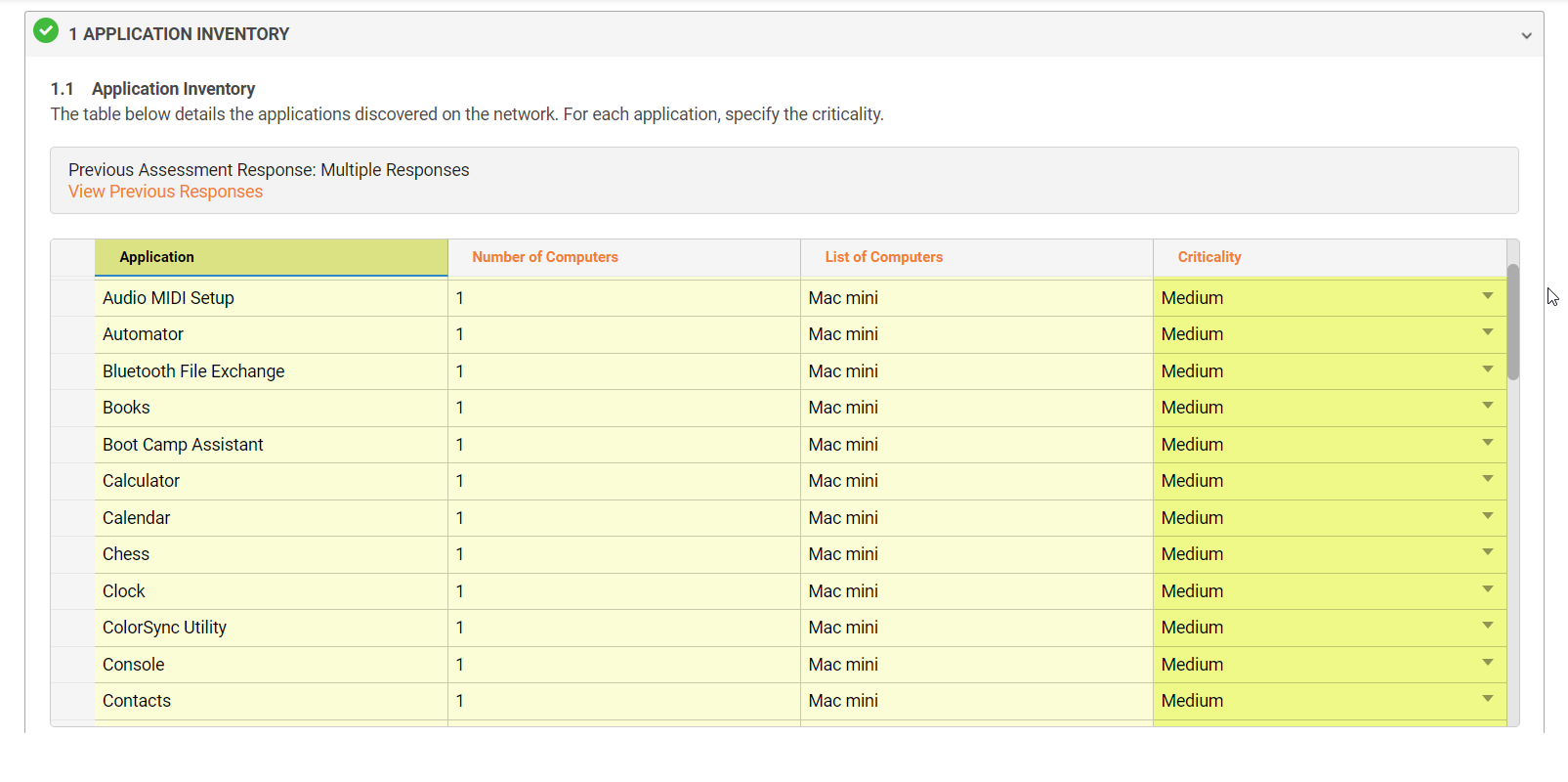
Introducing the Game-Changing CM GRC - macOS Computer Technical Review Assessment
This week we released the macOS Computer Technical Review Assessment for Compliance Manager GRC, a frequently requested feature for MSPs and IT departments that manage IT environments that include Apple-branded computers.
This new feature is enabled by specialized macOS Discovery Agents that are installed on the devices and configured inside the RapidFire Tools portal. Once set up to run, the agents automatically feed the data into the appropriate Compliance Manager GRC site without any needed adjustments to network security settings.
Compliance Manager GRC then automatically generates a full Technical Review Assessment of the scanned computers, including details about user access, asset inventory and the application inventory. Several new reports are included with this feature, including a Technical Risk Assessment and a Risk Treatment Plan.
Discovered issues are added to Compliance Manager GRC’s interactive Plan of Action and Milestone to assign and scheduled remediation efforts.
Compliance Manager GRC Updates
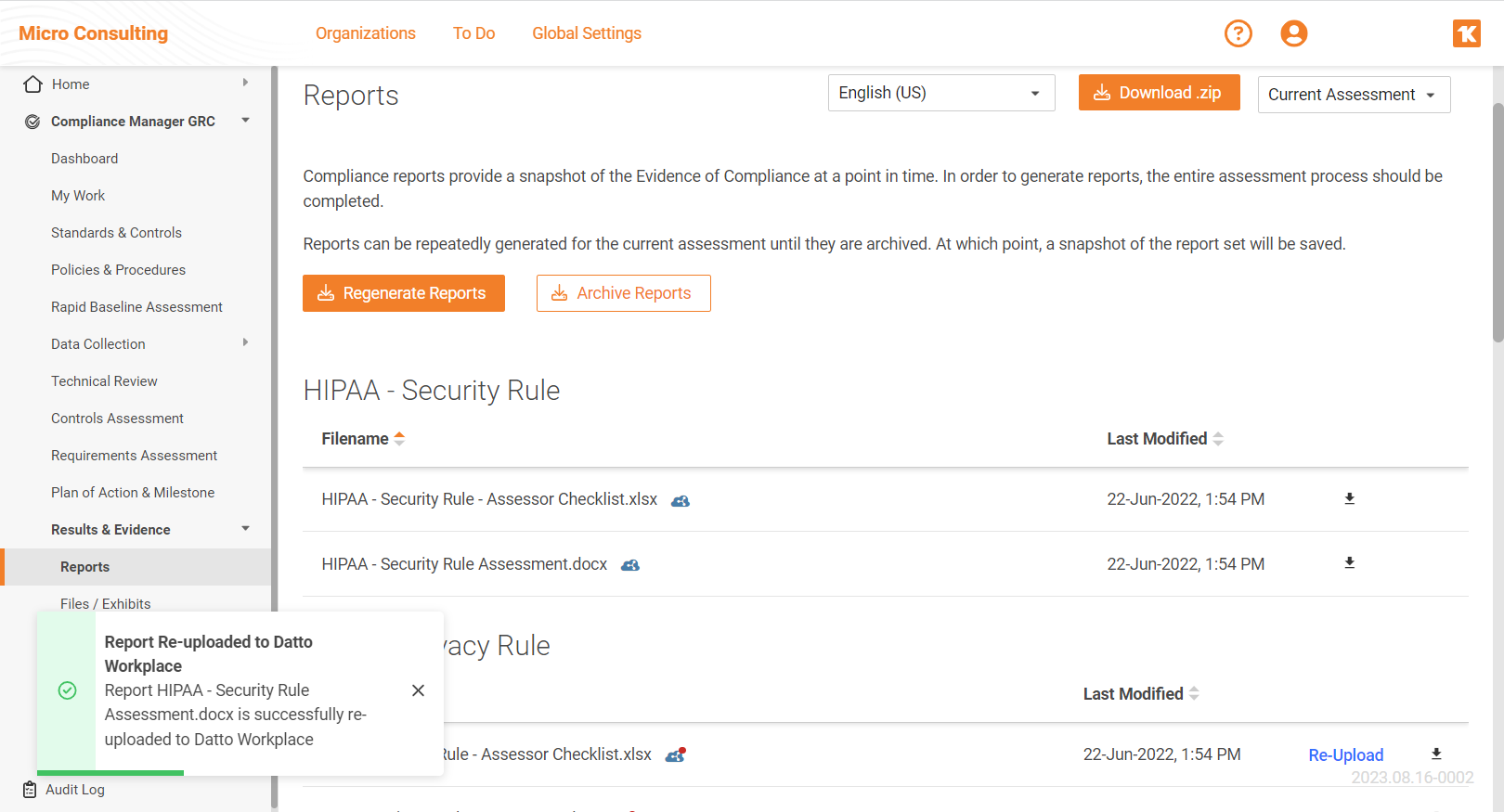
Streamlining Compliance Management with Compliance File Storage in Datto Workplace
If you use Datto Workplace, now you can use it to automatically store your documents generated by Compliance Manager GRC through a new seamless workflow we’ve just released.
This integration will be helpful for making compliance-related documents – such as Policies & Procedures Manuals Assessment Releases, and Evidence of Compliance more broadly available to external clients or internal stakeholders who don’t use, or have access to, Compliance Manager GRC.
Here’s why it’s so important:
Streamlined Workflow - Forget the hassle of regenerating and re-sharing compliance reports. With this integration, your clients can save valuable time and improve efficiency.
Seamless Integration - The sync between compliance reports and Datto Workplace ensures that teams can effortlessly access the most up-to-date versions of documents. Say goodbye to version drift and hello to consistency and accuracy.
Enhanced Productivity - Spend less time juggling compliance attachments across various repositories and more time on executing essential business changes for compliance audits.
This feature operates seamlessly in the background. Users set up a new set of credentials in Datto Workplace’s API, which facilitates the automatic upload of compliance reports from your Compliance Manager GRC site to Datto Workplace. To ensure data integrity, a conflict detection mechanism triggers every time a user accesses the Reports page in Datto Workplace, swiftly resolving any accidental modifications with the original source report from Compliance Manager GRC. Reports are uploaded discreetly in the background, so users will see the results only when revisiting the Reports page.
The Compliance File Storage in Datto Workplace feature is already live and available for use.
Compliance Manager GRC Updates
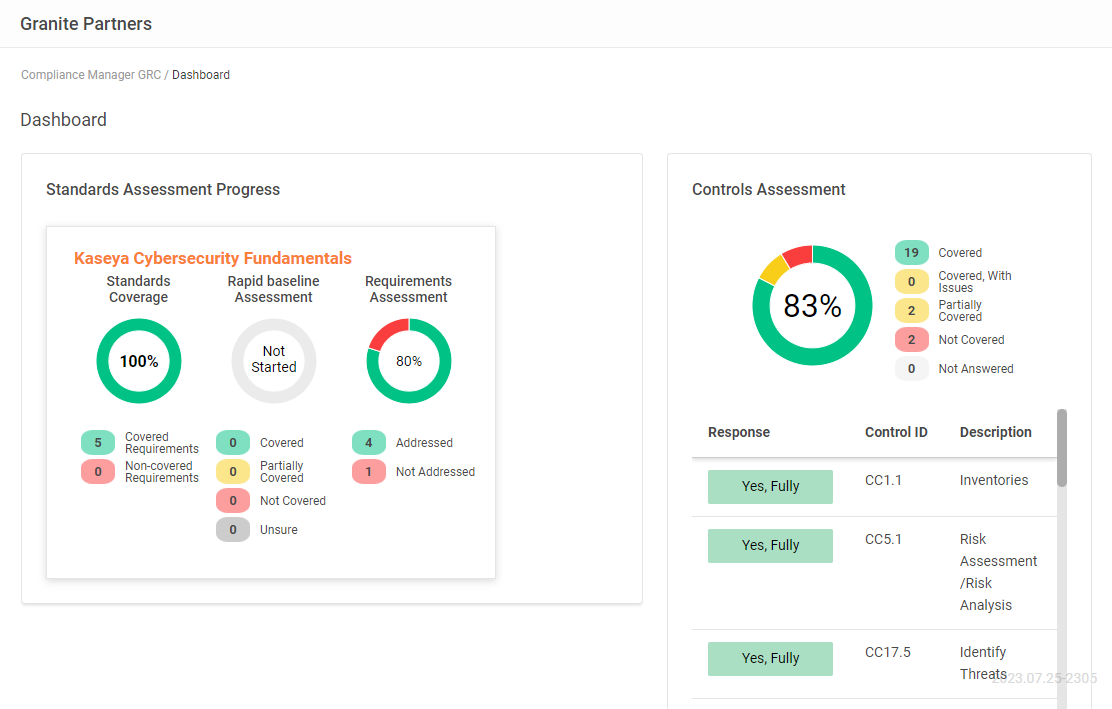
Introducing the Kaseya Cybersecurity Fundamentals: Your Simplified IT Security Framework
We’ve just added a unique new standard in Compliance Manager GRC that will help you elevate IT security assurance for networks where there is no formalized IT security program in place.
The new Kaseya Cybersecurity Fundamentals standard offers a streamlined framework for a basic cybersecurity assessment to serve as a launching pad for progressive IT Security improvement.
This entry-level standard is inspired by the NIST Cybersecurity Framework’s core principles, while harnessing the full power of Compliance Manager GRC’s automated data collection features.
Key Benefits for IT Professionals and MSPs:
- Effortless Onboarding: Designed for rapid adoption, enabling both IT professionals and MSPs to establish a standardized and automated IT security assurance program swiftly.
- NIST Framework: Built on the pillars of the NIST Cybersecurity Framework, ensuring a solid foundation for comprehensive security practices that resonate with industry standards.
- Faster Data Collection: Leveraging Compliance Manager GRC’s automated data collection capabilities, making the process seamless and efficient for all users.
- Customization for MSPs: Tailored to address the unique needs of Managed Service Providers, enabling them to offer enhanced cybersecurity services to their clients.
- Value-Added Service: For MSPs, the framework becomes a powerful tool to differentiate their offerings, attracting clients who prioritize robust cybersecurity measures.
Why It Matters:
- Accelerated Setup: Empowering IT professionals and MSPs to hit the ground running with Compliance Manager GRC, reducing setup time and complexity.
- Robust Foundation: Based on proven NIST CSF principles, offering a reliable basis for robust security measures.
- Efficiency Unleashed: Making the most of Compliance Manager GRC’s automated data collection, freeing up time for strategic security decisions.
Compliance Manager GRC Updates
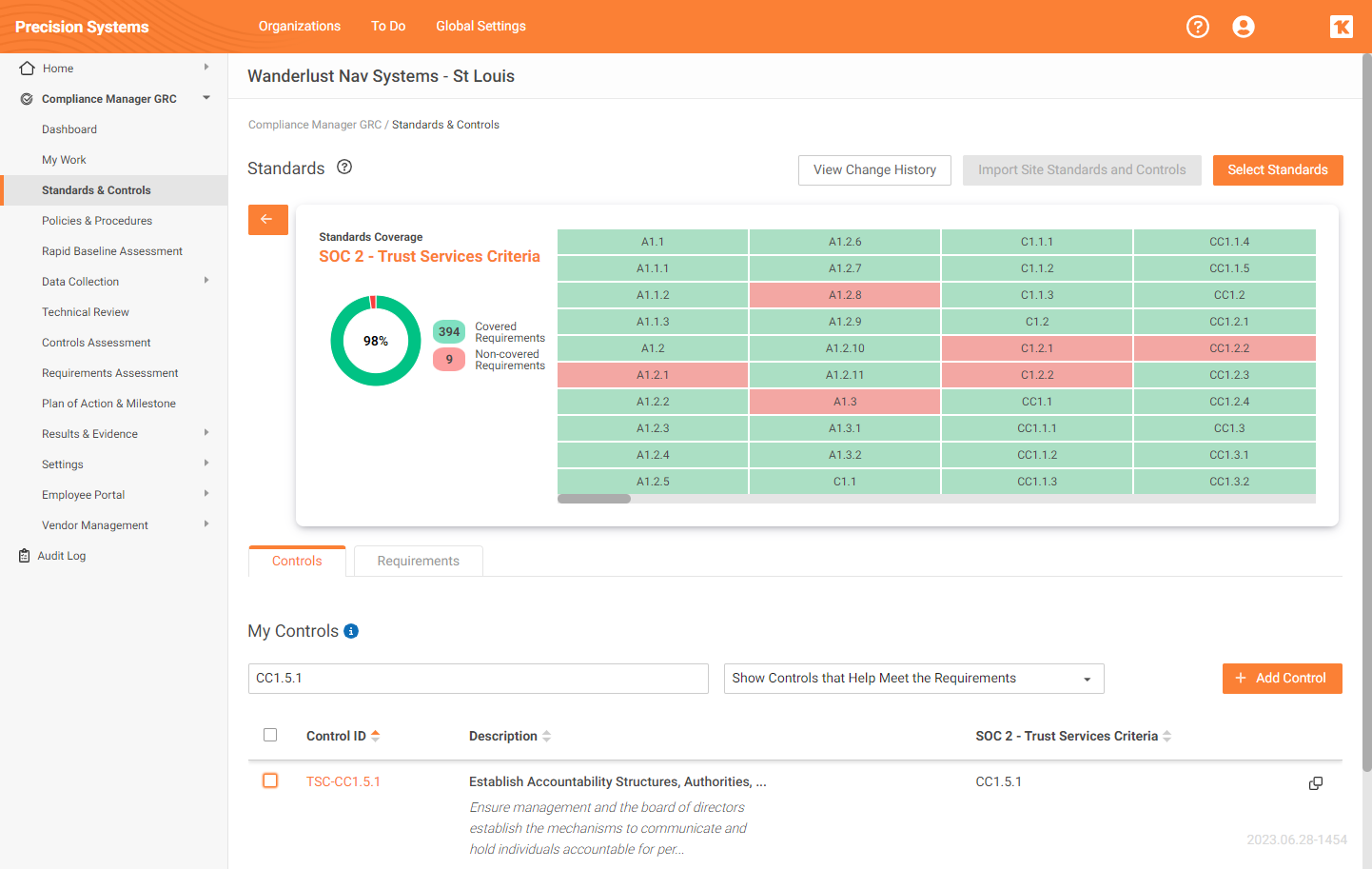
Manage SOC 2 Readiness with Compliance Manager GRC
The SOC 2 Trust Services Criteria is now included in Compliance Manager GRC, and ready for you to use to get ready for your SOC 2 exam by a certified auditor.
The Compliance Manager SOC2 Trust Services Criteria Template streamlines the journey towards obtaining a SOC 2 attestation report following the simple process:
-
Select the SOC2 - Trust Services Criteria Standards and Controls in any Compliance Manager GRC Site.
-
Generate a set of SOC2 - Trust Services Criteria Policies and Procedures manual to review all of the requirements.
-
Perform a Rapid Baseline Assessment, Controls Assessment, and Requirements Assessment to identify all the gaps and gather evidence of compliance.
-
Generate and use a Plan of Action and Milestones to assign tasks to subject matter experts and key stakeholders, and track progress.
-
Generate assessment reports that may be used as a business’s Information System Security Plan.
-
Generate the Auditor’s Check List for your certified independent auditor to speed the attestation and reporting process.
To learn more about the AICPA Trust Services Criteria and SOC 2 compliance, we encourage you to explore the following resources:
Compliance Manager GRC Updates
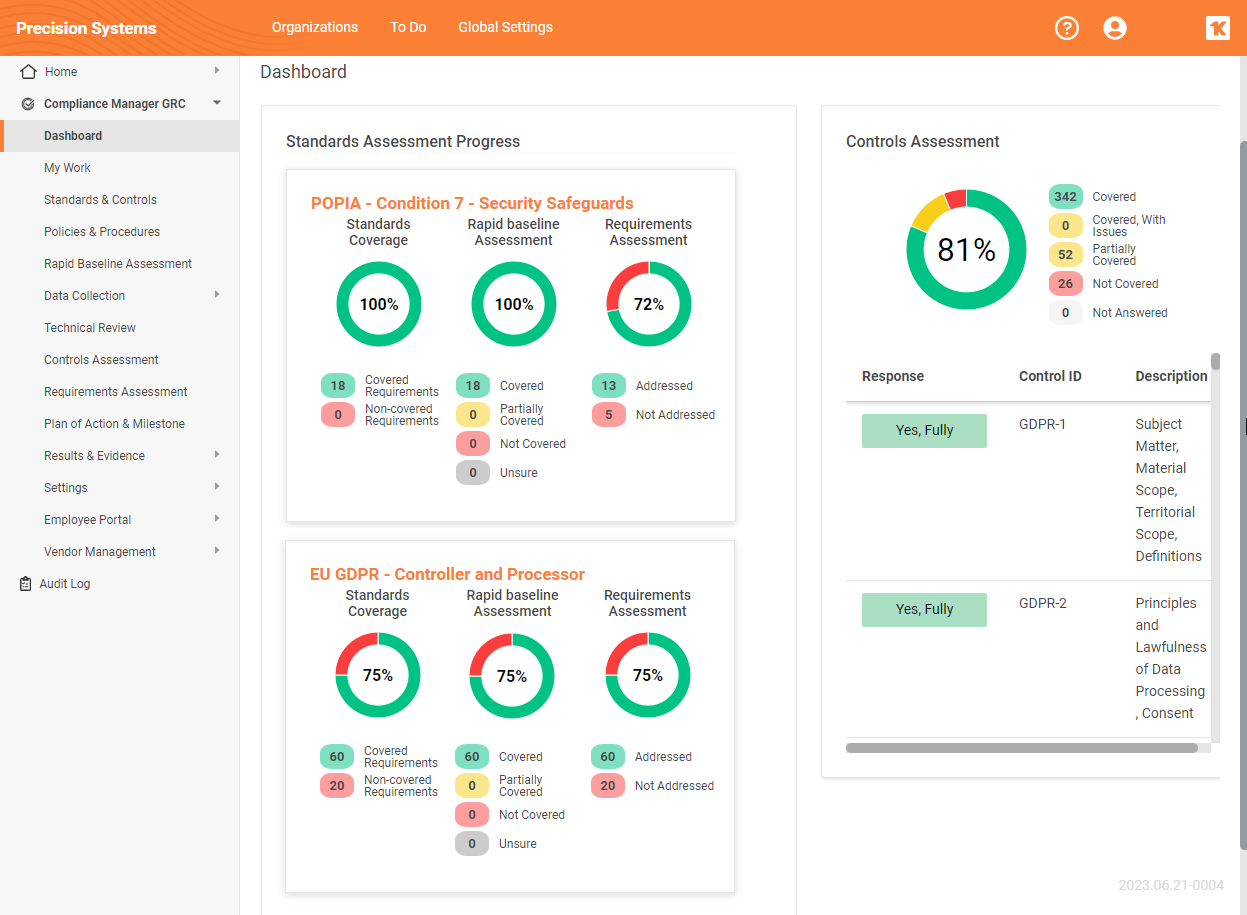
New Regulatory Standard for the Protection of Personal Information Act (POPIA)
We have added to Compliance Manager GRC a new standard – the South African national consumer protection law called the Protection of Personal Information Act (POPIA). Our standard covers Condition 7 of the Act, which includes all of the IT Security Safeguards requirements.
Compliance Manager GRC users can now perform an in-depth assessment of an organization’s compliance with the security safeguards specified in POPIA Sections 19, 20, 21, and 22 of POPIA’s Condition 7. These sections tackle critical issues like the integrity and confidentiality of personal information, measures to prevent loss, damage, or unauthorized access to information, and the importance of adhering to information security practices and procedures.
This feature comes complete with a full suite of tools to guide you through the compliance process. You can generate a set of POPIA Condition 7 - Security Safeguards Policies and Procedures, perform Rapid Baseline Assessments, Controls Assessments, and Requirements Assessments, and even generate a Plan of Action and Milestones for your organization.
Our new POPIA feature allows MSPs and SMB IT Technicians to streamline the compliance process, effectively manage risk, generate policies and procedures documents, divide assessment survey tasks, provide evidence of your organization’s compliance with the POPIA regulations.
CyberHawk Updates
Get Automated Alerts on Newly Discovered Internal Vulnerabilities
We have released a new feature for Cyber Hawk subscribers - Internal Vulnerability Alerts via VulScan. This feature focuses on change detection services, providing subscribers with immediate alerts on any changes identified within network’s internal vulnerabilities.
Cyber Hawk users will now be able to:
- Schedule the import of internal vulnerability data from VulScan appliances on a daily or less frequent basis.
- Include changes detected against policies for internal vulnerabilities in daily alert emails, weekly notice emails, and weekly or monthly summary emails.
- Include changes detected against policies for internal vulnerabilities in notifications that create tickets in a PSA.
The Internal Vulnerability Alerts feature leverages our VulScan technology to provide automatic alerts about changes in network’s internal vulnerabilities. This feature streamlines and automates the process, saving subscribers time, energy, and manual audit efforts. Please note that existing Cyber Hawk customers are already able to install an appliance to run internal vulnerability scans.
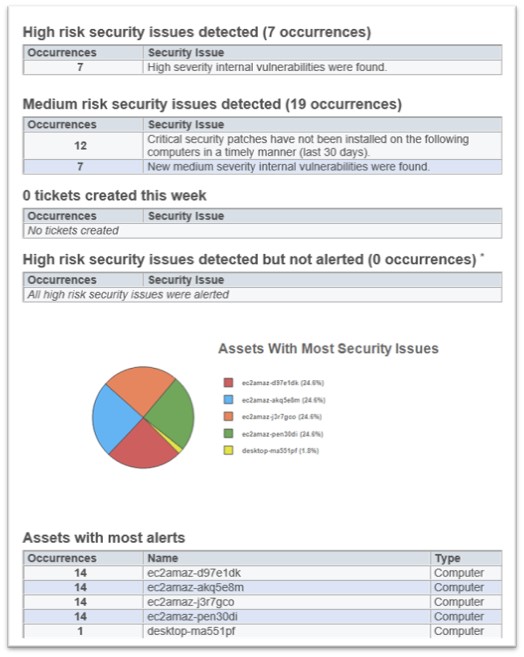
Change detection for internal vulnerabilities via VulScan provides MSPs or MMEs, that manage security or monitoring services for businesses the ability to measure changes related to potential compromises on the computers and servers on their client’s network, thereby saving valuable time that would otherwise be spent on manual audits.
Compliance Manager GRC Updates
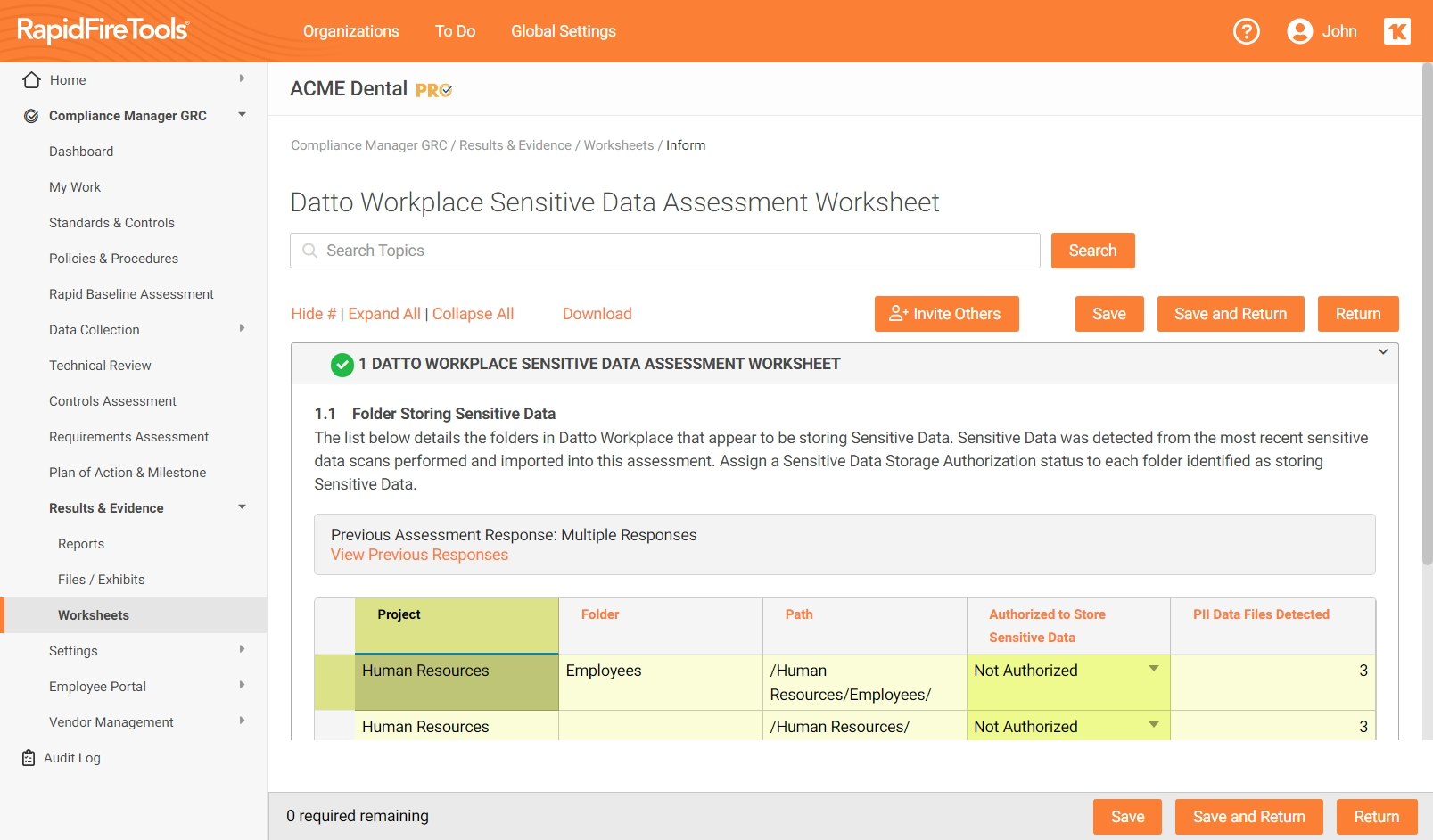
Introducing Sensitive Data Worksheets and Reports via Datto Workplace for Compliance Manager GRC
This week’s release includes an update to the Sensitive Data Worksheets and new reports fed by data from Datto Workplace, which provides a significant reduction in time spent collecting data for compliance audits.
For Datto Workplace customers who are responsible for tracking and reporting on sensitive data stored in their IT environment, managing compliance with that requirement is a huge challenge without a structured process and the right tools.
This seamless integration streamlines the compliance audit process by logging the types, names and locations of sensitive stored in each designated team in Datto Workplace, and feeding it to Compliance Manager GRC in the form of worksheets and exhibits for compliance audit submission.
Upon completion of a Technical Review Assessment in Compliance Manager GRC, users can generate client-friendly worksheets and supporting documents detailing sensitive data stored in Datto Workplace, which include:
- HIPAA ePHI data, GDPR privacy data, PII (information that can be used to distinguish or trace an individual’s identity, either alone or when combined with other information that is linked or linkable to a specific individual), and PCI card holder data
- Types and names of files containing sensitive data and their locations in Datto Workplace
Compliance Manager GRC now also automatically creates issues in the Plan of Action and Milestones (POA&M) to address detected sensitive data.
For this integration to work, Datto Workplace customers must also have Network Detective Pro, which is powering the PII discovery function in Datto Workplace.
Compliance Manager GRC Updates
Append Data to Technical Review Worksheets
If you have additional authorized users, assets or applications to add to worksheets after the automated data collectors have completed their scans, now users can manually add rows to the worksheets to manually append more data.
This additional flexibility makes it quicker and easier to update your worksheets when changes take place between your regular assessments, and adjust for devices that are off-line.
Entries that are manually added to the worksheets are included when the Assessment Supporting Documents are generated. The appended information will be appropriately labeled as “Other Authorized Users”, “Other Authorized Assets”, and “Other Authorized Applications” in the respective worksheets and reports.

Compliance Manager GRC Updates
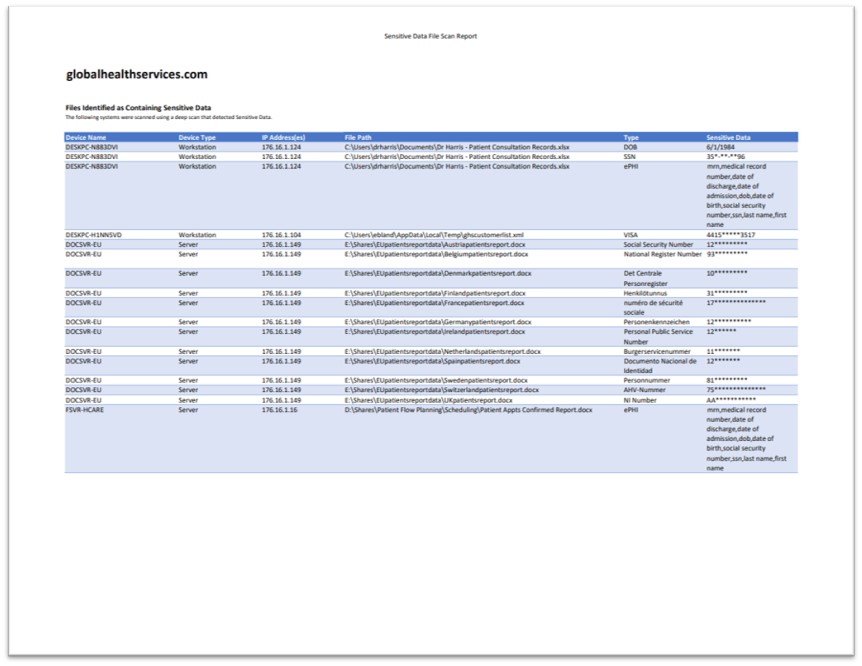
Sensitive Data & Drive Encryption Assessment
Compliance Manager GRC now supports a specialized network scan designed to meet the data privacy of many standards, including HIPAA, GDPR and PCI, as well as adhering to the data privacy recommendations established by the NIST Cybersecurity Framework.
The Sensitive Data & Drive Encryption Assessment helps IT professionals and MSPs automatically identify, manage, and secure sensitive data, and to generate evidence of compliance with specific types of data sets including: Electronic Protected Health Information (ePHI); Payment Card Industry Data Security Standard (PCI DSS) Cardholder Data; Personally Identifiable Information (PII); and General Data Protection Regulation (GDPR) Personal Data.
It also checks whether specific drives and devices are encrypted to protect authorized sensitive data locations.
The functionality of this feature includes:
- Setting up Organizational Discovery Agent Deep Scans - These scans identify computer assets that store sensitive data and determine the computer’s disk and disk volume encryption status.
- Performing a LAN or Azure Cloud Scan - This scan identifies any sensitive data stored on these networks.
- Creation of Interactive Sensitive Data Assessment Worksheet - listing all locations of discovered sensitive data, type of sensitive data, and encryption status. Users indicate whether the the users and locations are authorized.
- Performing a Technical Review - This review uses the imported data to generate a Sensitive Data Assessment Worksheet and a File Share Identification Worksheet.
- Generating a Plan of Action and Milestones (POAM) - This POAM includes a list of identified Data Security Issues that require addressing.
- Generating Assessment Reports - These reports provide detailed information about the detected data security issues, the locations of sensitive data files, the permissions of network share locations, and the encryption status of drive volumes.

Improved Data Collection for Linux and macOS Devices
Data collection for macOS and Linux computers just got a whole lot better with our new and improved Local Data Collectors and Discovery Agents.
With this update, MSP’s and IT technicians can run a local data collector on the latest macOS and Linux devices or install the new Network Detective Pro Discovery Agents for enhanced data collection in macOs, Linux, and mixed OS environments. The enhanced data collectors support both macOS Intel X64 and ARM (M1/M2) chipsets.
The enhanced data collected by the new agents and local data collectors is comparable to the data collected by their Windows counterpart and is used to augment the Network Detective Pro Full Detail Report, Full Detail Change Report, Excel Export, and Asset Detail Report.
Compliance Manager GRC Updates
FTC Safeguards Rule Standards Compliance Management Template
This release includes a new compliance management template to help organiations streamline the process of meeting regulatory requirements of the Federal Trade Commission’s Standards for Safeguarding Customer Information – the Safeguards Rule, for short. The new rule takes effect on June 9, 2023 and requires, for the first time, a wide range of companies, put into place cybersecurity programs to protect their customers’ personal and financial data.
The new FTC Safeguards rule template allows Compliance Manager GRC users to:
- Run an initial baseline assessment to identify any gaps in the systems in place, and the requirements of the FTC Safeguards Rule.
- Generate a standard FTC Safeguards Rule Policies and Procedures manual.
- Perform a detailed risk assessment that checks the status of every control (or safeguard) associated with the FTC Safeguards Rule requirements.
- Create dynamic a Plan of Action and Milestones to manage and track the compliance process.
- Generate comprehensive set of reports.
The new rule impacts a number of businesses that you might not immediately think of as “financial institutions.” In addition to Community Banks. Credit unions, Mortgage lenders and brokers, the rule also applices to companies that offer car loans, furniture layaway plans, payday lenders, check cashers, tax preparers and accountants, Collections agencies, real estate and property appraisers, and many more types of businesses that have access to personal financial information.

Network Detective Pro Updates
Streamline IT Security Risk Assessments With This New Feature!
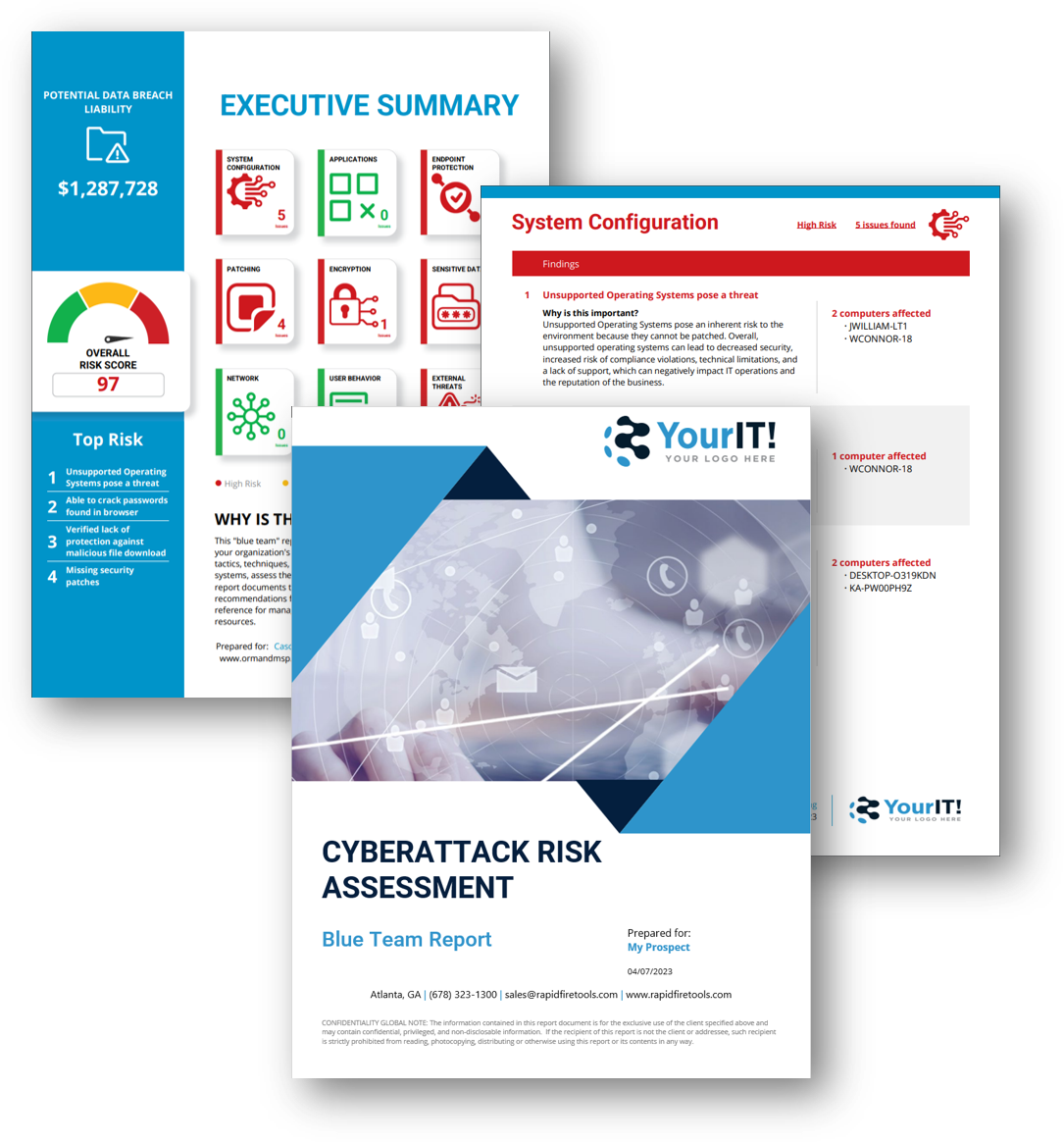
Cyberattack Risk Assessment is a new feature for Network Detective Pro that allows MSPs and IT Departments to run quick, easy and safe automated cyberattack risk assessments on any remote or local computers.
The feature includes three key components:
-
A white-labelled download page that you can brand with your logo
-
A non-intrusive, self-running testing tool that end-users can run on their computers with nothing to install, and no special credentials
-
A purpose-built assessment report that highlights the top risks discovered using charts and plain-English descriptions summarizing the impact and importance of hardening the network. It also supplies supporting technical details about the specific issues it uncovers.
For Managed Services Providers, the main use case for this feature is to make it easier to sell your services. With very little labor, you can remotely spot-check any prospect network for hidden vulnerabilities on selected computers, and then use the report to help demonstrate the need for better risk management.
IT Departments that manage their own networks can use the same tool to spot-check the cybersecurity posture of your strategic partners and vendors, and also check on remote computers used employees who use their own devices for work. Your can also use the tool for internal spot check security audits, and as a great executive report for management.
Compliance Manager GRC Updates
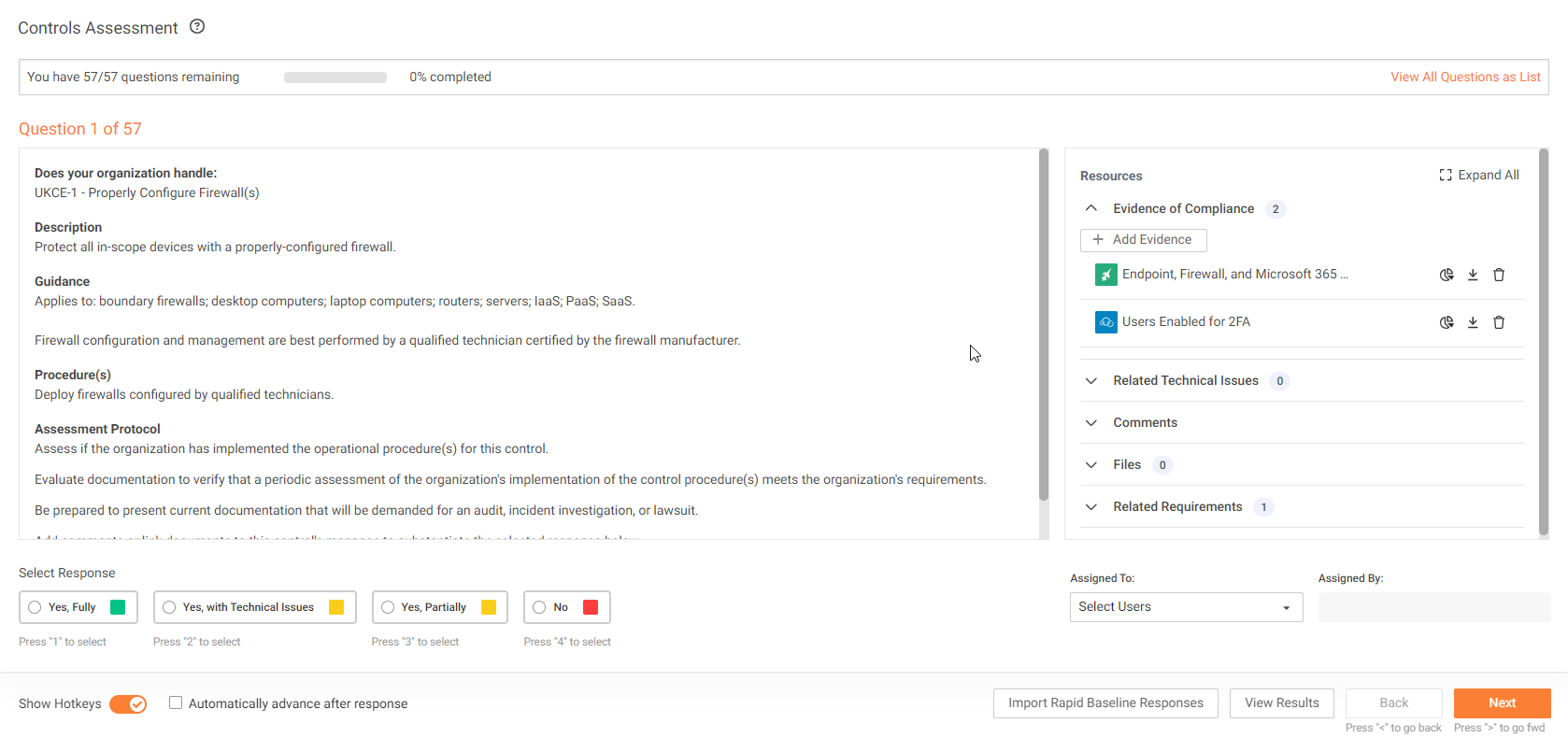
Easily augment Compliance Manager GRC messaging with the Enhanced Guidance Editor
This week’s release introduces the Guidance Text Editor, a feature designed to elevate your Compliance Manager GRC experience. This functionality allows users to create Custom Guidance and incorporate a more tailored approach to managing the Compliance Assessment process.
By overriding the default CM GRC Guidance content found in Standards and Controls with customized guidance content, this feature provides greater flexibility in aligning Compliance Manager GRC with the unique requirements your clients.
During the Compliance Manager GRC assessment process, users will be able view the Custom Guidance when performing the:
- Rapid Baseline Assessment
- Controls Assessment
- Requirements Assessment
The Guidance Text Editor is particularly advantageous for (MSPs), as it enables them to:
- Create more comprehensive guidance that references their own best practices and services while also considering their clients’ existing Governance, Risk and Compliance practices.
- Develop client-specific guidance, ensuring a more effective and streamlined assessment process for their clients’ subject matter experts.
By utilizing the Guidance Text Editor, MSPs can significantly improve the efficiency of the Compliance Management process, ultimately delivering more value to their clients.
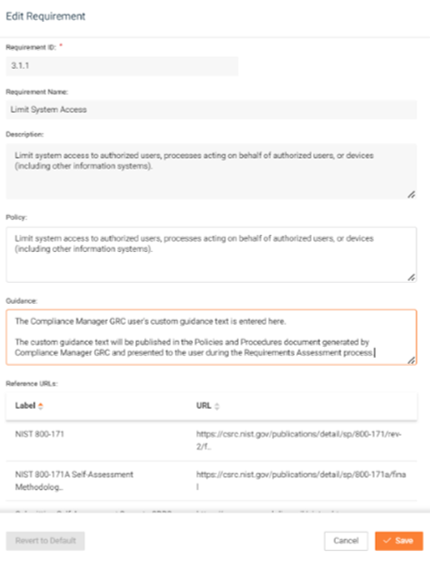
Introducing In-App Editing of Policies and Procedures in Compliance Manager GRC
Custom Policies and Procedures, released on April 13th, enables users to create, modify, and instantly publish custom policy and procedure text in Compliance Manager GRC generated documents, streamlining the process of aligning your organization’s existing policies with the tool’s capabilities.
With this latest enhancement, you can:
- Create custom policy text for any built-in requirement language.
- Create custom procedure text for a requirement’s related operational control.
- Immediately generate and publish custom content in Compliance Manager GRC generated Policy & Procedure documents.
- Instantly view and use custom procedure text during Rapid Baseline Assessment and Controls Assessment processes.
- Select Policy & Procedure documents to be included with the generated Assessment Reports
- Access a Standards and Controls Change History log that records site setup settings and customizations made to requirements policies and related control procedure text.
This feature upgrade gives users the power and flexibility to edit the controls and requirements directly inside the Compliance Manager GRC, dramatically improving your ability to customize frameworks and standards to match your exact policies and procedures for a given site.
Compliance Manager GRC Updates
New IT Security Framework Compliance Template: CIS Critical Security Control v8
This week’s release helps MSPs, and IT professionals align their cybersecurity programs with the best practices defined by of Center for Internet Security (CIS). The last updated framework is version 8 of the CIS’s Critical Security Controls categories.
The framework is broken down into three different “Implementation Groups (IGs)” based on the nature of the organization and reliance on information technology. Each IG includes an increasing number of safeguards within the controls. Compliance Manager GRC includes done-for-you compliance process management templates for all three
The framework, often referred to simply as “CIS V8” for short, is the private sector’s alternative to the federal government’s framework: NIST CSF. Many MSPs and IT departments find that the CIS V8 framework is equally effective, but easier to implement and administer. Compliance Manager GRC also supports NIST CSF.
For both frameworks, Compliance Manager provides the option for a Rapid Baseline Assessment, with built-in interactive questionnaires, plus comprehensive assessments of each control and requirement. As with all standards, Compliance Manager GRC’s also includes a highly automated process for collecting assessment-related data, producing dynamic worksheets, and automated plans of actions listing tasks that must be completed to achieve compliance.
It also allows you to track progress and collaborate with subject matter experts, stakeholders, and auditors through an online portal, and generates updated policies and procedures manuals and evidence of compliance at the click of a button.

Network Detective Pro Updates
New Datto “Hero” Report Available Inside Network Detective Pro
This week’s update for Network Detective Pro is the Datto Unified Continuity Report, the first (and currently only) report that consolidates backup data from all four Datto Continuity services, including Siris and Alto (BCDR), Cloud Continuity for PCs (CC4PC), and Datto Continuity for Microsoft Azure (DCMA). This new report, available only through Network Detective Pro, consolidates back-up information from all four Datto products and summarizes it in a unified, brandable report that can be presented to managers and executives as evidence of the otherwise “hidden” back-up activities.
We call this a “Hero” report because both MSPs (Managed Services Providers) and IT professionals need a way to generate periodic reports quickly and easily to their respective stakeholders that demonstrates their back-up responsibilities are being met. IT professionals who use Network Detective Pro and Datto Continuity can now include a brandable “back up success report” that looks and feels like the other Network Detective reports they produce.
With this report, MSPs can easily showcase the results of their continuity services, thereby building trust with their clients and demonstrating their expertise in the field. IT managers can also benefit from this feature as they can produce reports to review with business stakeholders, providing them with valuable insights into the organization’s continuity environment.

Compliance Manager GRC Updates
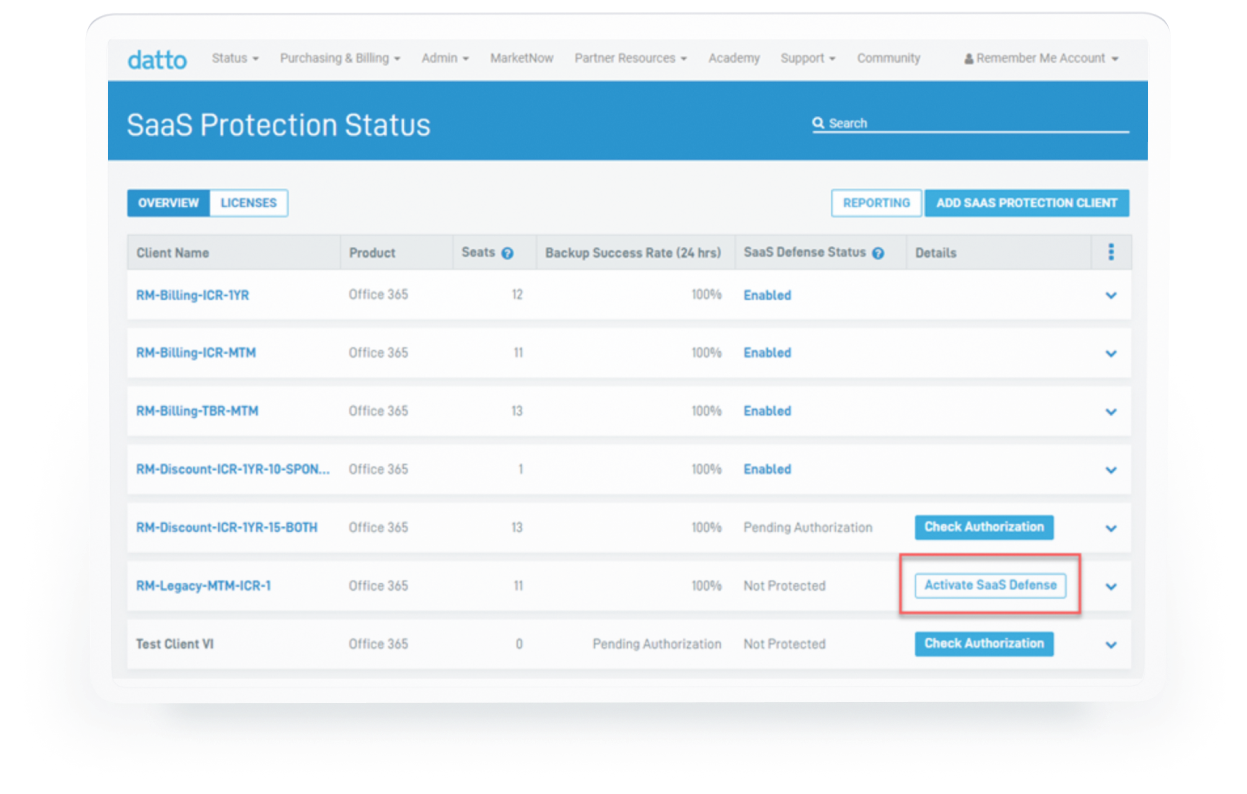
Streamline Collection of Your SaaS Backup Evidence of Compliance
This week’s release includes a new workflow integration between Datto SaaS Protection and Compliance Manager GRC. This new integration streamlines the collection of evidence of compliance with any security control that includes a SaaS backup requirement.
As part of the standard Compliance Manager GRC assessment process, if the Datto SaaS Protection integration is turned on, the system will pull in the back-up status of any assets stored in Microsoft 365 or any Google-based storage devices. An “evidence” file will be automatically generated and stored as an “Exhibit” in the Compliance Manager GRC Site’s Files and Exhibits document storage area.
This workflow automation eliminates the need for IT professionals to manually pull reports out of the Datto SaaS protect portal in the event of an audit, and saves time by compiling all compliance-related evidence documents in one place.
For MSPs, this integration simplifies compliance reporting to clients as part of their compliance management service.
Network Detective Pro Updates
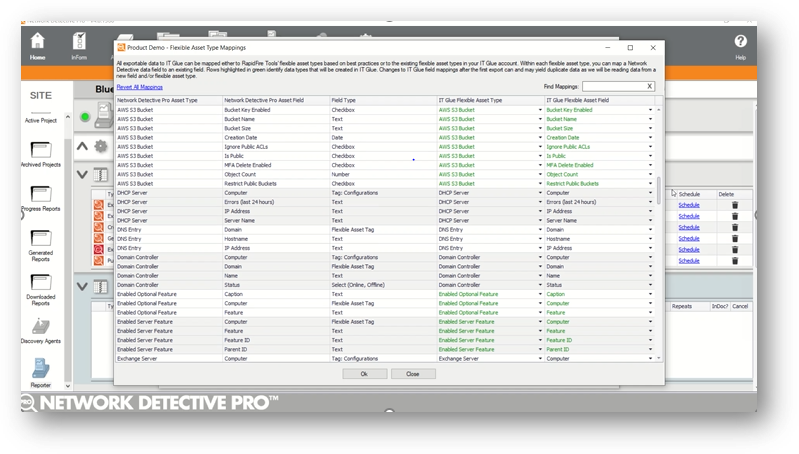
AWS Export to IT Glue
This week’s latest feature for Network Detective Pro allows MSPs and IT departments to automate the creation and maintenance of AWS documentation in IT Glue from within Network Detective Pro, reducing operational inefficiencies and saving valuable time for technicians.
This new cloud documentation automation integration is available in per-Organization and Global asset views. The new data entry, and ongoing maintenance of AWS documentation, covers the following information:
- Enabled Services
- EC2 (Computing power assets)
- IAM (User assets)
- RDS (Database server assets)
- S3 (File storage assets)
This feature also supports mapping AWS data to new and/or existing Flexible Asset Types in IT Glue.
Prior to this feature, documenting and maintaining AWS assets in IT Glue was a manual and time-consuming process. Updating documentation required auditing and could easily drift between the documentation and the real state of the system. AWS separates much of its infrastructure by region, which also added extra time and effort for technicians to navigate between different views for larger organizations or clients.
With the AWS Export into IT Glue feature, MSP or IT helpdesk technicians can now easily reference AWS assets in IT Glue where the rest of their documentation lives, saving time on support tickets. Updating existing AWS documentation in IT Glue is now a streamlined process.
Network Detective Pro Updates
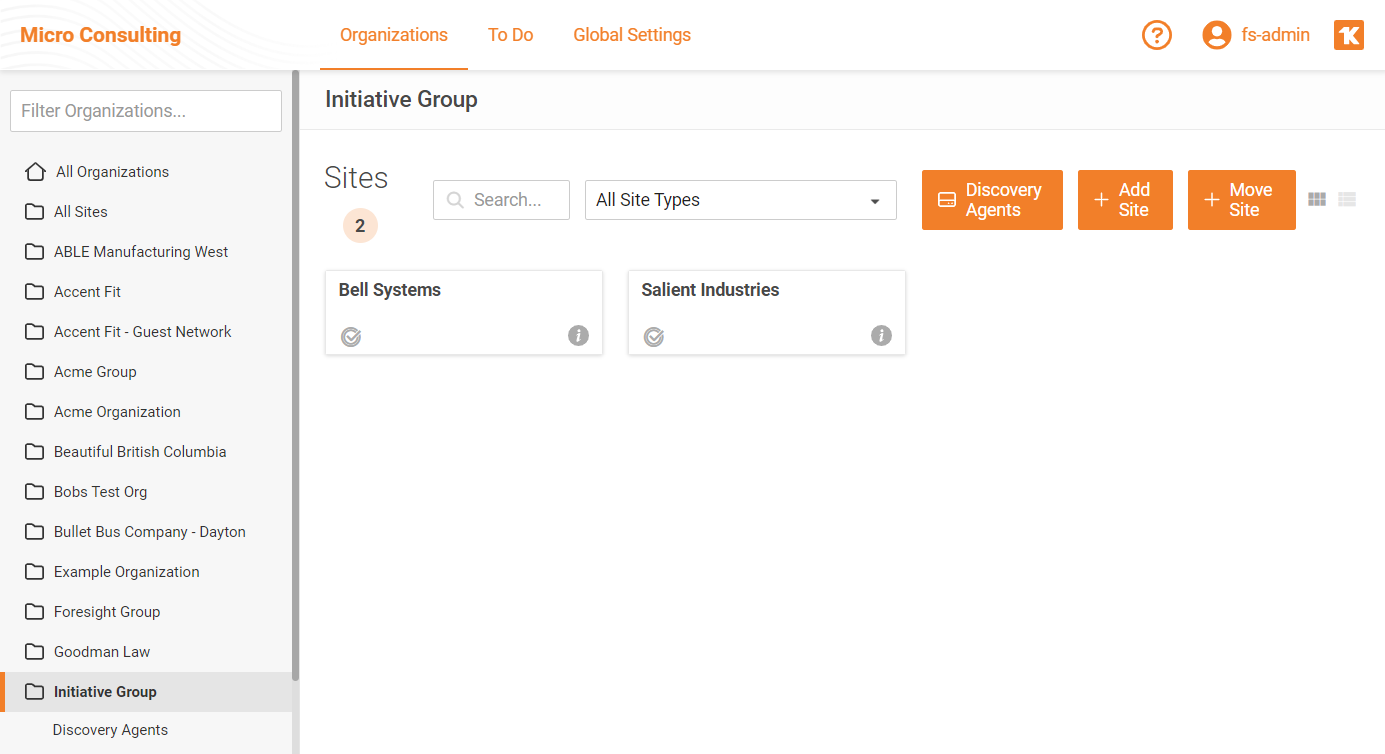
Network Detective Pro Organization Discovery Agents
This feature streamlines data gathering for organizations by allowing a single Discovery Agent installed on a computer to be used by all sites set up within an organization. This feature is useful in situations where an organization is setup with VulScan and/or Compliance Manager GRC sites in addition to Network Detectve Pro. This allows a single discovery agent to run computer scans to feed all three products.
As part of this release, for Network Detective customers with sites that were originally set up with no organization, a new organization will automatically be created for each site, using the same name. Once the organization is set up, the new Organization Level discovery agents can be deployed.
By using the same Discovery Agent for on-going data collection on an individual computer, users with multiple RapidFire Tools subscriptions will streamline data gathering for organizations, saving time and resources to maximize their software investment.
Compliance Manager GRC Updates
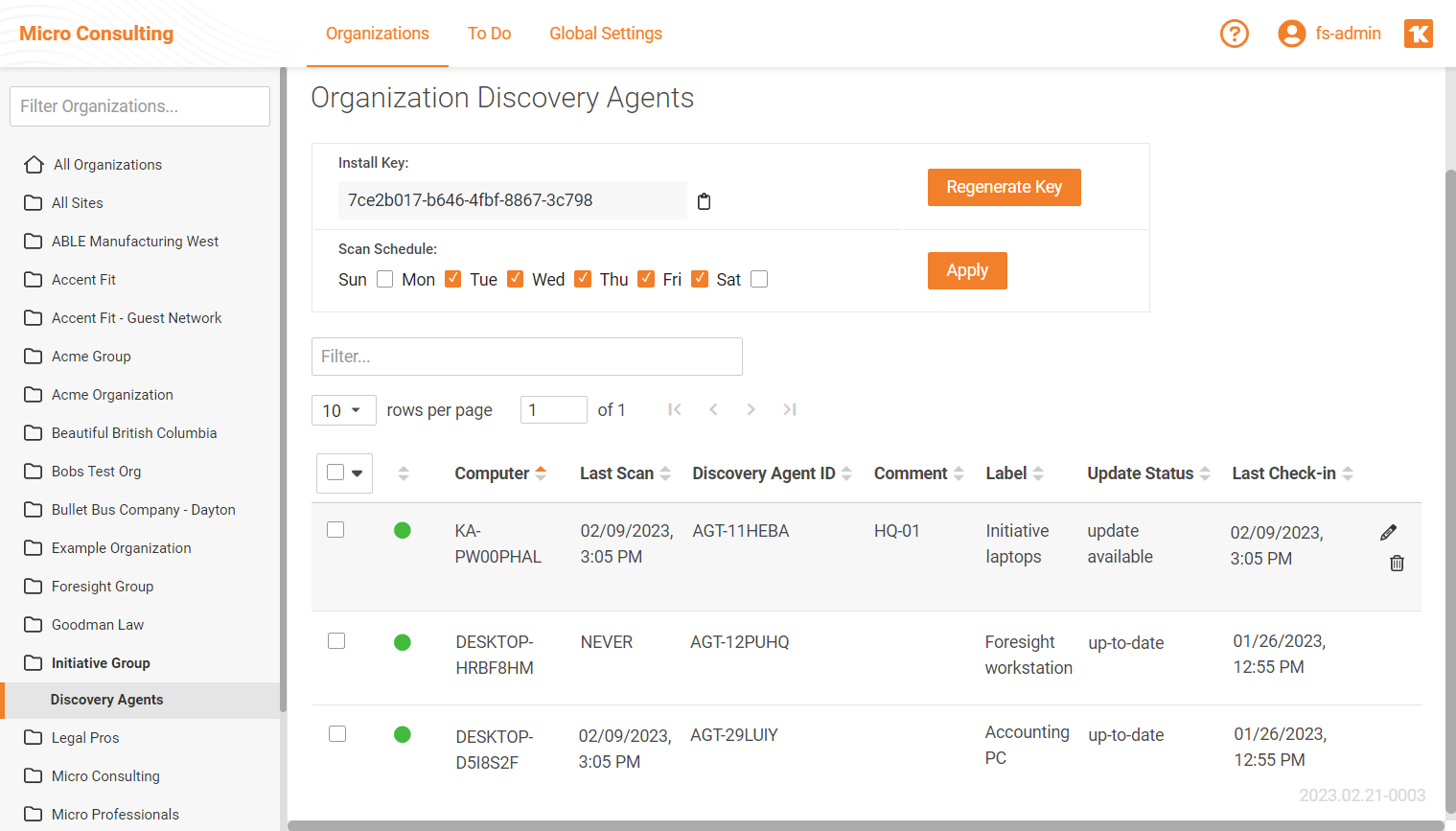
Introducing Compliance Manager GRC Windows Computer Discovery Agents
This week’s release includes new Windows Computer Discovery Agents which make it easier to collect data from individual Windows machines as part of a Compliance Manager GRC assessment. These light-weight agents are installed on the computers to be scanned, eliminating the need to change configurations to WMI and other protocols that might block or interfere with the local data collectors.
This additional method of data collection gives Compliance Manager GRC users more flexibility when it comes to performing automated assessments as part of the compliance process. The Windows Computer Discovery agent will capture the same information that is discovered by the local data collectors, with the exception of the deep PII (personally identifiable information) scan.
Discovery Agents are set up at the Organization level and support all RapidFire Tools products. As a result, a single agent running on a computer can run scans for Network Detective Pro and VulScan in addition to Compliance Manager GRC.


VulScan Updates
Introducing PSA Ticket Creation in VulScan
This week’s release includes an update to Vulscan gives you more granular control over which network vulnerabilities discovered by VulScan get pushed into your PSA service ticket system.
With just a click of a button, VulScan users can now create individual service tickets inside of Autotask, BMS and other PSA solutions directly from the Issue Detail screen within the web-based VulScan management portal. This new workflow innovation provides significant improvements in “remediation efficiency” by eliminating the creation of tickets that don’t require any action.

Previously, the VulScan system could be configured to automatically create tickets of all discovered issues after each scan. However, with this latest enhancement, technicians have the opportunity to review and triage each issue before deciding whether to create a service ticket, mark the issue as a false positive, or ignore it. Anytime a ticket is created, the issue detail screen will be updated with the ID# for the ticket that was created, along with its status.

For a look at some of our other VulScan features with mini demos, visit https://www.rapidfiretools.com/products/vulnerability-scanner/features/.
Network Detective Pro Updates
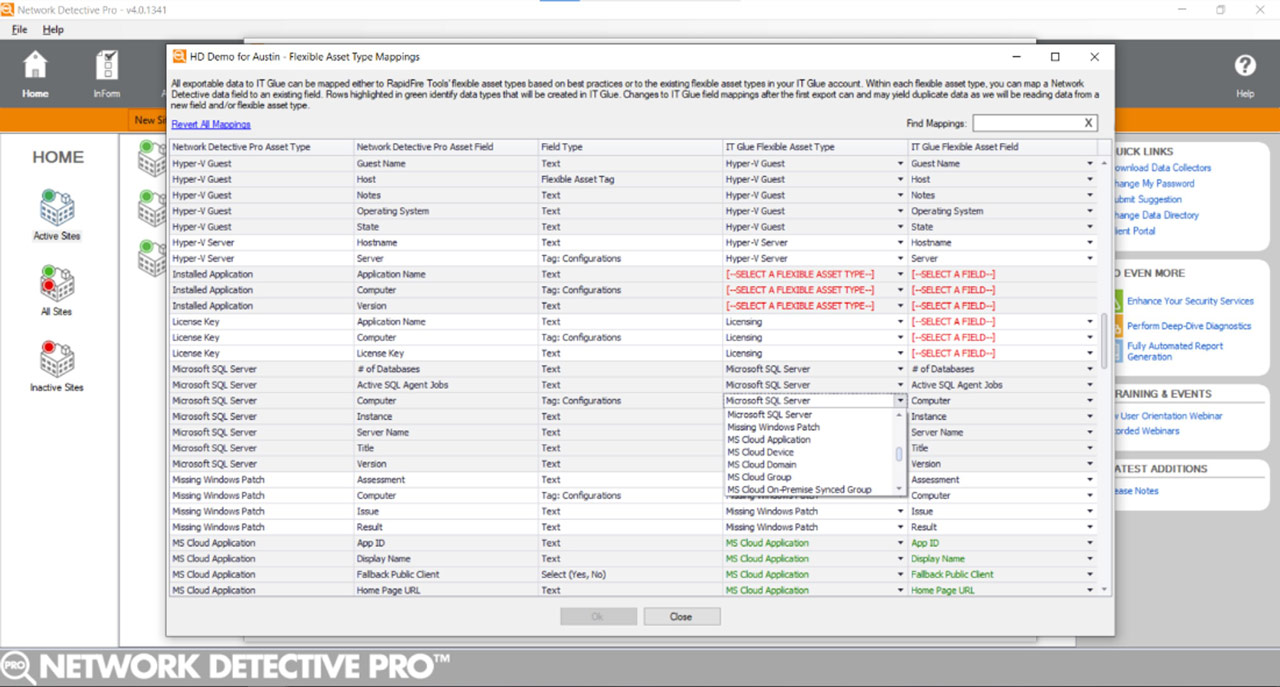
Custom Date Export into IT Glue Flexible Asset Types
Get ready to supercharge your workflow with the latest Network Detective Pro feature: Custom Data Export into IT Glue’s Flexible Asset Types.
This workflow integration makes it easier then ever to manage your network, endpoint, and user data. With the new field mapping page inside Network Detective Pro makes it incredibly simple to configure certain types of data such as Active Directory and Microsoft Cloud data for export into IT Glue.
The field mapping screen includes a dropdown of your IT Glue Flexible Asset Types, granular field mapping prompts, and an intelligent verification engine that identifies any previously-broken mappings. This new feature gives you complete control over the organization of Network Detective Pro data inside of IT Glue, and saves time on every subsequent export.
Network Detective Pro Updates
Prospecting is a snap for Datto Partners with our new BCDR Needs Analysis
Datto partners who have Network Detective Pro new have a powerful new way to quickly expand their book of Datto BDCR business. In this latest release, we include an automated process for quickly scoping out the on-premise back-up requirements for any existing client or prospect, and generating a dynamic proposal with details of the recommended Datto solution. The report also includes a recovery time calculator, and summary information on the servers and workstations on the network.
In addition to the actual Datto BDR Needs Assessment report, the data gathered by Network Detective Pro can be used to discover issues related to backups that could cause loss of data in the event of a disaster, opening the door to upselling other services along with Datto solution.
Network Detective offers two versions of this feature:
-
Quick Version - Is extremely efficient and only requires responses to a minimal set of questions to augment the automated data collection.
-
Full Version - Which is more flexible and detailed analysis, allowing for exclusions of drives and partitions from the generated proposal.
The new feature is a free value-added upgrade to Network Detective Pro. Key benefits include:
- Quickly perform BDR Needs assessments to identify and expand BDR sales opportunities
- Identify the Risks associated with the prospect’s current BDR solution that is in place to present the business impact of system downtime and recovery time
- Calculate Recovery Time Costs associated with prospect’squo;s current BDR to justify BDR system upgrades or improvements along with generating a BDR System Sizing specification
Not a Datto partner yet? You can still run the assessment on your existing client networks, and then talk to your Account Manager about how much more money you can be putting in your bank with a fleet swap.
Compliance Manager GRC Updates
Automatically Generate Evidence of Compliance with Back-up Requirements in Compliance Manager GRC
Our latest workflow integration accesses the back-up logs created by several Datto products, and automatically incorporates them as evidence of compliance with the back-up requirements of any standard tracked in Compliance Manager GRC.
This connection adds another layer of automation to the compliance management process. It eliminates the time wasted by technicians who currently have to manually pull back-up logs and upload that documentation into Compliance Manager GRC to serve as evidence.
This new integration adds value by saving the IT technicians time during the compliance assessment process and enhances the accuracy of evidence of compliance for internal and external audits.
The integration currently works with Datto SIRIS, Datto ALTO, Continuity for Microsoft Azure (DCMA). Customers must have subscriptions to one of these products and Compliance Manager GRC to access the integration.

Network Detective Pro Updates
Simplify Data Collection with End-user Initiated Computer Scans
There’s a new data collection tool for Network Detective Pro that makes it quick and easy to selectively scan individual computers without the need to run local data collectors.
Simply provide any end-user with a special link that they can click on to initiate the scan on their own Windows computer. The scan runs automatically, and then sends the collected data back to Network Detective Pro to be automatically combined with other data collected from the same site.
This new feature allows you to either send the custom link to the end-user by email, or you can send them to a download page that you can customize with your company logo. With a couple of clicks, end-users can initiate the scan without any technical knowledge or complicated instructions. The is automatically performed in the background, and the resulting scan file is uploaded to the RapidFire Tools portal.
End-User initiated scans are a great prospecting tool for the savvy MSP and a value-added resource for IT Departments with WFH Employees.


Network Detective Pro Updates
Save Time with Organizational Updates from IT Glue
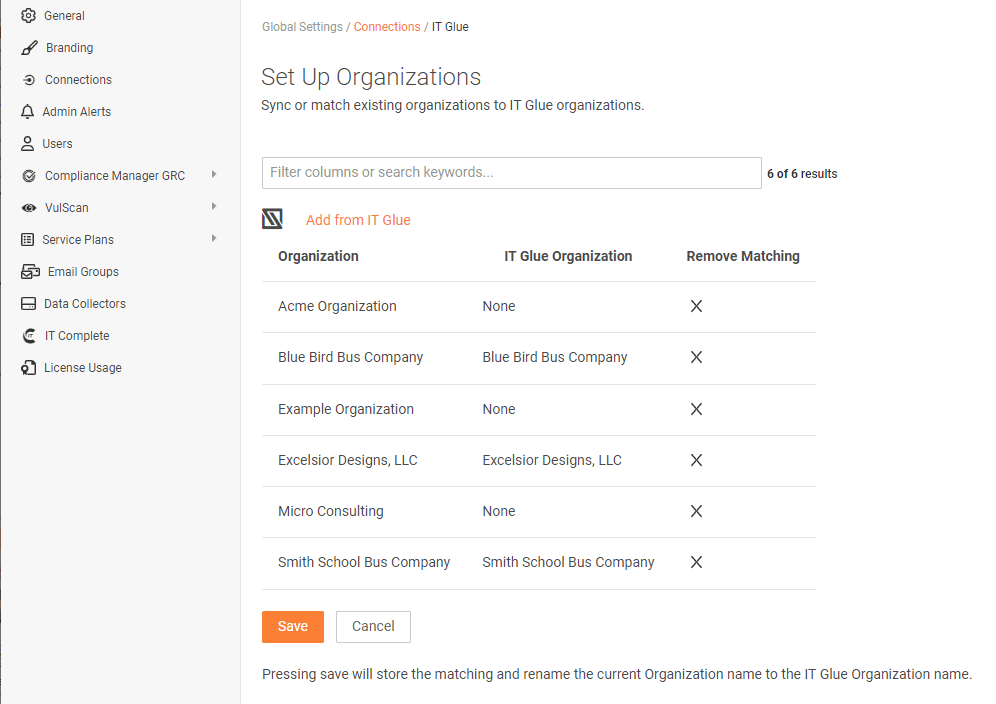
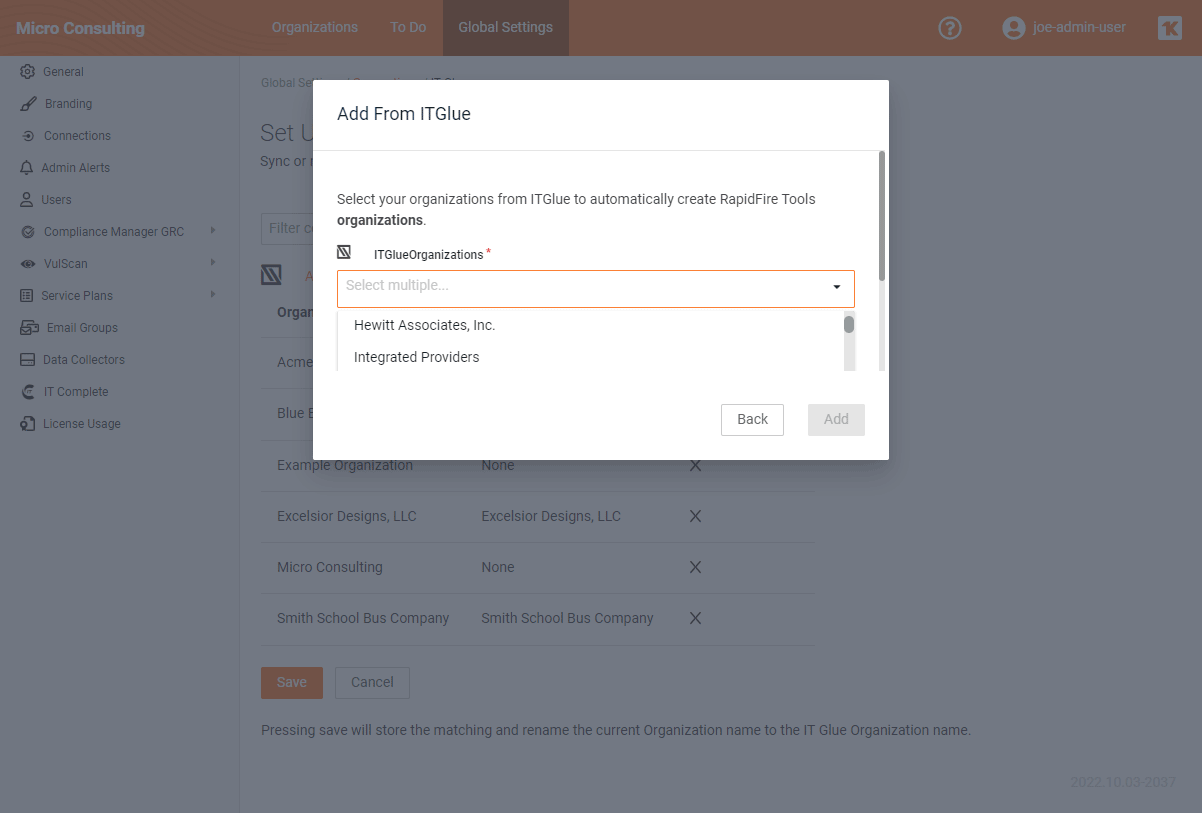
If you use IT Glue, we just made it easier for you to onboard new organizations inside of all the RapidFire Tools applications, and also to automatically sync up any changes to your client organization information across all your RapidFire Tools apps. It also means that when IT Glue customers sign up for any new RapidFire Tools solutions, all of your existing client organizations will automatically flow in from IT Glue.
This latest workflow integration with IT Glue reduces the time it takes IT Technicians to set up new RapidFire Tools products they buy. As soon as you log into any RapidFire Tools product with this integration turned on, you’ll see all your client organizations flowing in from IT Glue. Similarly, if you are already using any RapidFire Tools product – and also have IT Glue – any time you onboard a new organization, all you need to do is set up the organization in IT Glue, and you’ll see that client organization showing up in the RapidFire Tools portal.
Similar integrations are also available in most other Kaseya products as part of our “IT Complete” platform. With this integration turned on, IT Glue becomes the “master” source of organization information. So, when you change the client organization information in IT Glue, it will automatically update the same organization info across all Kaseya products. The goal is to keep finding ways to improve your efficiency and make your life easy!
Compliance Manager GRC Updates
Get Compliance Expertise and Project Management with Compliance Services Pro
Compliance Services Pro is a new professional service now available to subscribers of Compliance Manager GRC. Offered by Kaseya’s professional services team, the new service provides additional subject matter expertise and project management staff that takes over the “heavy lifting” associated with Compliance Management. They can help with HIPAA, CMMC and PCI compliance.
Here’s what you get with Compliance Services Pro, all for one low fixed cost:
- Guidance from high-level compliance experts without paying exorbitant consulting fees
- Support of a large team of project managers, eliminating the need for you to hire new staff
- Help with getting the right stakeholders (across various departments of your client’s organization) engaged in the assessment process by optimizing the use of Compliance Manager GRC’s role-based architecture
- Enhanced in-product guidance that will be automatically made available in your Compliance Manager GRC software
- Assistance with delivering compliance reports to your clients
Bringing in Compliance Services Pro as your compliance delivery partner is the proven way to enhance the security posture of your clients while also containing your own costs. Whether you already deliver compliance services or are just starting out, we can help you with two levels of CS-Pro’s service — Standard and Premium — depending on your needs.
The service includes an automatic upgrade to your Compliance Manager GRC sofware to include enhanced “Pro Guidance” that appears as you complete the compliance questions.
VulScan Updates
Expanded Vulnerability Detection with New VulScan Discovery Agents
IT professionals can increase security and reduce risk by installing the new lightweight VulScan Discovery Agents on all Windows machines in the IT environment – including remote computers and those connected to the network.
We have recently released a new feature of VulScan that expands the scanning depth of our vulnerability management tool. The new VulScan “Discovery Agents” can be installed on individual Window-based computers and can scan them for vulnerabilities in the Windows operating system and in the Microsoft applications installed on the computers.
The Discovery Agents are designed to supplement the VulScan internal network vulnerability scanners, which can pick up these same vulnerabilities if the target computer is connected to the network, and the application is in use at the time of the scan. However, network scanners can’t detect vulnerabilities on remote computers that are not attached to the network, nor can they detect vulnerabilities on connected devices that have their own local firewalls turned on, or if the target applications are not in active use.
The Discovery Agents supply an extra layer of security, by enabling IT professionals to detect Windows-based vulnerabilities on remote computers, as well as on networked computers that are blocked or where the target applications are dormant.


Compliance Manager GRC Updates
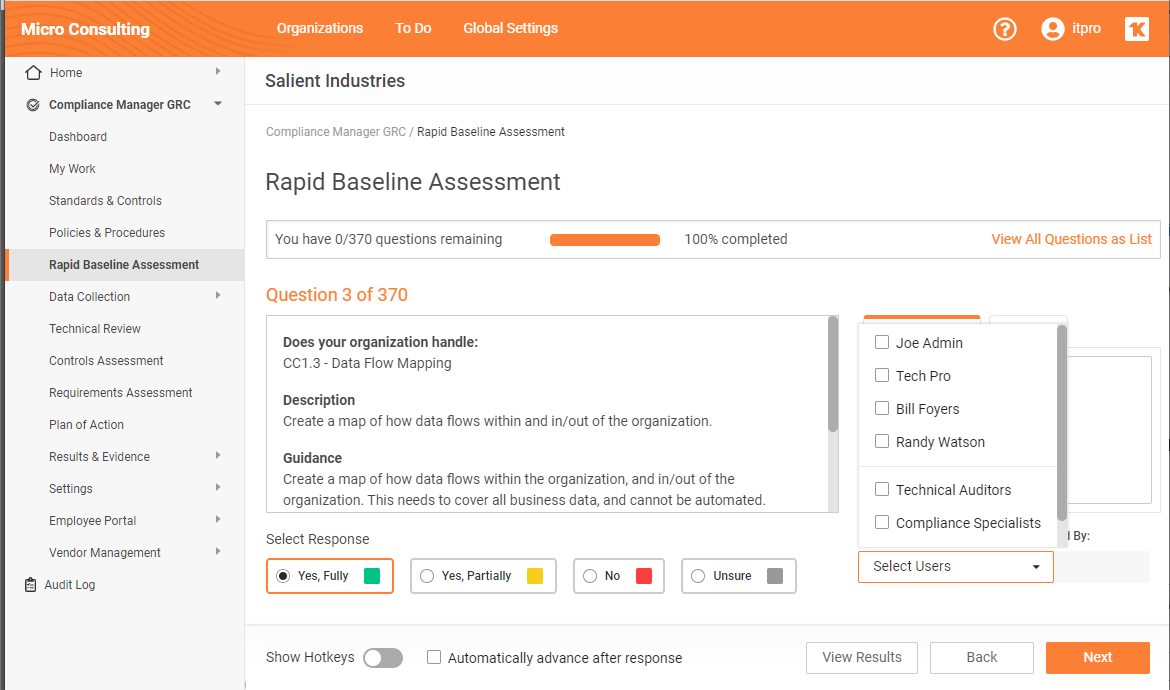
Engage The Right People On The Right Tasks With Role Based Task Assignments
Compliance Manager GRC now includes the ability to help IT professionals manage compliance by assigning specific assessment questions to an individual or group of individuals. This allows the IT staff to handle the technical questions, and assign the rest to subject matter experts and other stakeholders. The result is assurance that compliance assessments are more accurate and complete.
Some of the elements of this new feature include the ability to:
- Create Groups and add users to groups
- Assign individual questions (in the Control Assessment the Requirement Assessment and the Rapid Baseline Assessment) to an individual or group
- Assign to more than 1 group
- Mass assign in the List View of the Control and Requirement Assessments
- Output the assignments in the Assessment Checklist and in the Assessment Report
This new functionality optimizes the compliance task process by ensuring individuals or teams focus on questions relevant to their roles, reducing the time required for assessments. Compliance Manager GRC helps you reduce risk and improve efficiency while juggling compliance with all your IT security requirements.
Network Detective Pro Updates
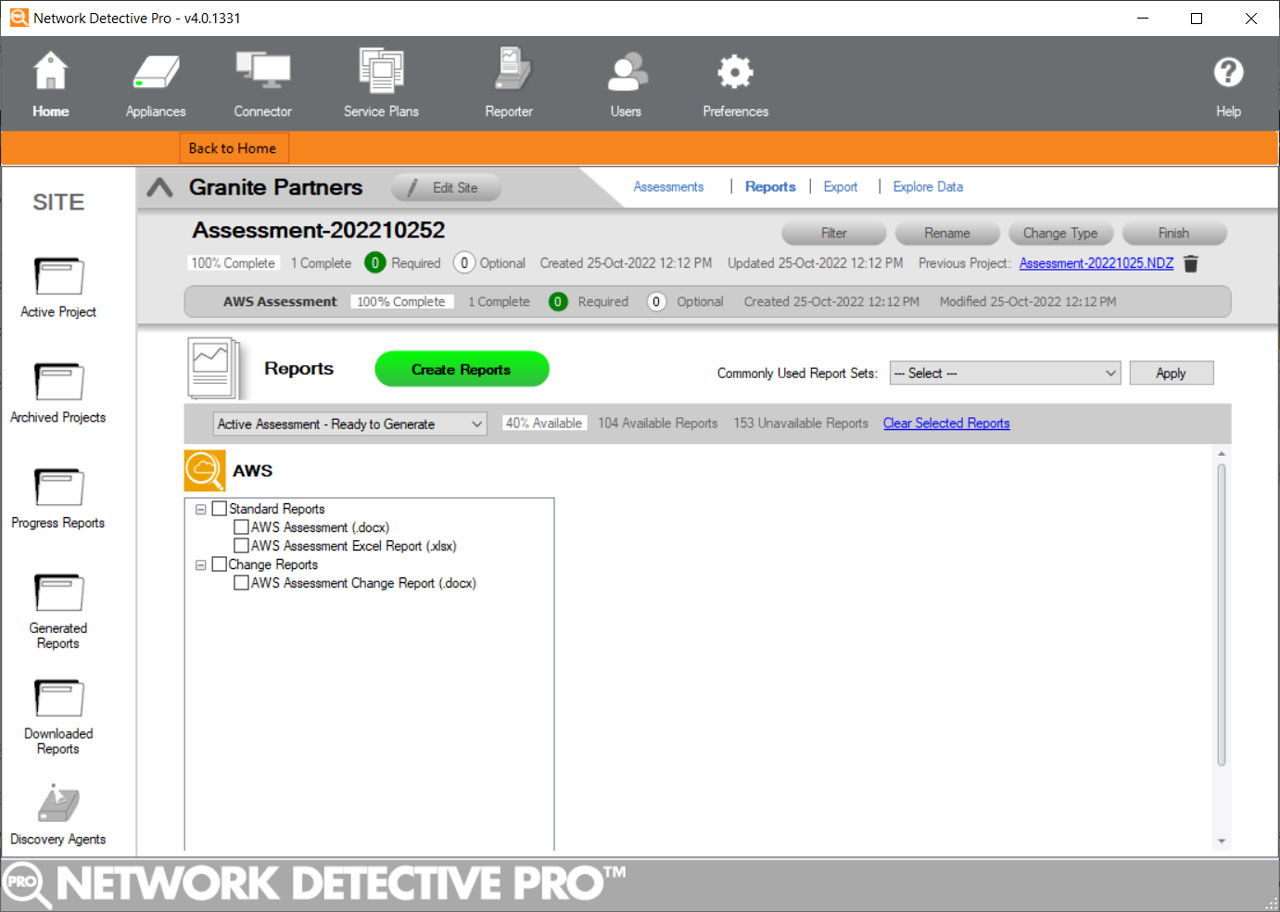
Network Detective Pro Cloud Assessments Now Include AWS
Amazon Web Services (AWS) is the largest cloud computing platform, offering 200+ universally featured resources, from infrastructure to machine learning. These combinable systems provide maximum usability and are designed expressly for the optimization of your application’s performance through content delivery features, data storage, and more.
The Network Detective Pro IT Assessment landscape has been expanded to include Amazon Web Services (AWS), adding another important component to the Cloud Assessment capabilities of our software.
Users now have the ability to run an “AWS Data Collector” that will pull into Network Detective Pro basic infrastructure data out of the Amazon cloud, along with details from some of the most commonly used cloud services.
The AWS Cloud Assessment uses this information to produce three new editable detailed assessment reports.
- AWS Assessment
- AWS Assessment Excel Export
- AWS Assessment Change Report

The new reports include details about some of the following AWS settings and services:
- Account Settings – Basic information including the ID for the Account and Organization, which is useful when communication on behalf of the business to AWS.
- Contact Information – Shows the contacts on file for the AWS account
- AWS Regions – users of AWS can locate their resources in regions that are close to their customers for performance.
- Enabled Services - AWS has hundreds of services and growing all of the time. It is important to have awareness of which services are currently in use. It can also be used to identify unknown services that may be enabled
- Amazon IAM – Identity and Access Management - AWS Identity and Access Management provides secure access and management of resources in a secure and compliant manner. AWS accounts are typically provisioned with a root account, but it is recommended to use the Identity Access Management (IAM) service to add additional users and assign permissions. This section shows the various groups and users that have been granted access.
- Amazon VPC – Virtual Private Cloud - Amazon VPC enables you to set up a reasonably isolated section of the AWS Cloud where you can deploy AWS resources at scale in a virtual environment. Network resources can be grouped in VPCs. VPCs represent network segmentation in the AWS world. VPNs can be established to VPCs allowing external access to the resources.
- Amazon EC2 – Elastic Compute Cloud - EC2 is a cloud platform provided by Amazon that offers secure, and resizable compute capacity. This represents one of the most commonly used compute resources in AWS that can be used to run virtual machines. These are some of the first types of resources that MSPs are typically asked to manage in the AWS environment for their customers. In most cases, RMM agents can be placed on individual virtual machines that are part of EC2.
- Amazon RDS – Relational Database Service - Amazon Relational Database Service (Amazon RDS) makes database configuration, management, and scaling easy in the cloud. This service is used to creation relational databases in the cloud (like SQL Server and MySQL). Businesses typically have migrated their databases from on premise to RDS instances in AWS.
- Amazon S3 – Simple Storage Service - Amazon S3, at its core, facilitates object storage, providing leading scalability, data availability, security, and performance. This service is used to store files in AWS for access by various other services, including EC2. Additional uses can be for downloads, uploads, and also to host websites.
With Network Detective Pro, you’ll have access to all the AWS data you need to prioritize your work and get the right things done at the right time. Unlike other reporting tools, Network Detective Pro gives you the power to control the output. You decide which reports you want to run. You brand them with your company logo, your contact info, your colors and your choice of image and layout. You can even edit and customize them to your heart’s content.
Compliance Manager GRC Updates
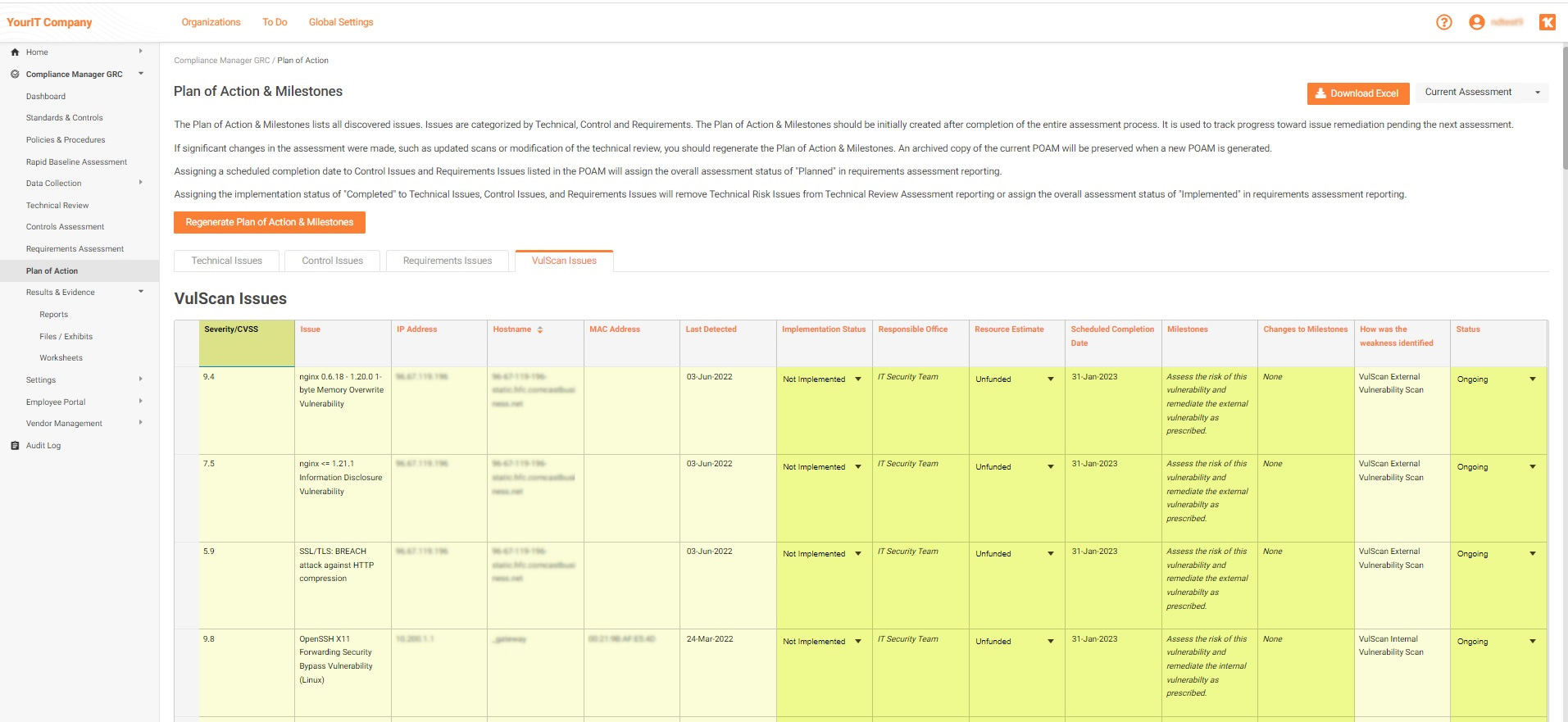
Maintain VulScan Itemized Tasks inside of CMGRC
Compliance Manager GRC now includes the ability to help IT professionals manage remediation of IT security vulnerabilities that may impact an organization’s compliance with regulatory standards by integrating VulScan Itemized Tasks into the Plan of Action and Milestones.
This enhanced functionality is part of an existing workflow integration between Compliance Manager GRC and VulScan. Subscriptions to both products are required.
With the integration Compliance Manager GRC users can tap into the most recent scan data pulled by VulScan for a given site, and apply it against any standard that is being assessed. Plan of Action and Milestones (POAM) produced by Compliance Manager GRC will include a separate task for each High and Critical vulnerability discovered by VulScan.
VulScan Updates
New CVE ID filter improves vulnerability management
Vulscan now parses the Common Vulnerabilities (CVE) IDs out of the Greenbone feed description and drops it into is own field in the VulScan dashboard, giving you the ability to search and filter for specific vulnerabilities. By exposing the CVE ID for each vulnerability, you can now:
- Quickly search scan results to see if you’ve been hit by a specfic vulnerability,
- Use the CVE ID as part of your exclusion rules
- Easily copy the CVE ID and paste it into a search engine for supplemental information beyond what’s included in the built-in guidance.
A new widget has been added to the VulScan dashboard to show the top Critical and High Vulnerabilities by CVE.


RapidFire Tools Portal Update
New Option To Force Multifactor Authentication For All
The RapidFire Tools Portal is a web platform to access several modules, including VulScan, Cyber Hawk, Compliance Manager GRC and portions of Network Detective Pro. All these modules can share a common set of users and support a common set of organizations.
The portal has always supported the ability for users to set up multi-function authentication individually from within their settings. With this new release, there is a new option for Master Users to go into the Global Settings Menu and check a box to “Require Two-Factor Authentication” for all users.
Once enabled, all users will be prompted to set up multifactor-authentication upon their next log-in attempt, and taken directly to the user settings menu with set up instructions.
Network Detective Pro Updates
2 New Infographic Reports Fed by Workflow Integrations
We’ve just released two new IT Complete workflow integrations that pull data from different modules into Network Detective Pro to help IT professionals quickly report on key issues to their executive stakeholders and clients.
Vulnerability Scan Assessment Summary Report
This new high-level report is generated with data from the latest internal and/or external vulnerability scans from VulScan (VulScan subscription required). The report includes a donut chart showing the total number of vulnerabilities discovered by the last scan, as well as the proportional breakdown of Critical, High, Medium, and Low priority based on the CVSS score.
The report also includes the top five vulnerabilities discovered (if any) along with a brief description of the issue and the actual CVSS score. The reports can be used to either justify the need for more funding for more IT security measures to harden the network or, on the flip side, to justify the value of regular vulnerability scanning.

New Compliance Baseline Assessment Summary Report
With this latest workflow integration, you can now include the results of your Compliance Manager GRC Baseline Assessments right out of Network Detective Pro. This is a great way for IT professionals and MSPs to show executive management or client stakeholders where the organization stands regarding compliance with any standard or custom set of IT requirements.
Each report can display a high level baseline compliance assessment chart for up to three different standards. The charts include an at-a-glance view of the percentage of requirements that are fully covered, and a breakdown of those that are partially covered, not covered or “not sure.”
This report is a great way to take stock of the resources that will be required to both complete the initial rapid baseline assessment and better scope ongoing compliance requirements.

New Password Policies Summary Report
IT technicians are asked to establish password policies to enhance computer security by encouraging users to employ strong passwords and use them properly. Password policies are also often part of an organization’s official regulations and may be taught as part of security awareness training.
However, IT professionals need a quick and easy way to report to executives password policy compliance to help enforce the policies. This report provides high-level metrics comparing end-user password behaviors to industry standard best practices. Among the metrics compared are use of historical passwords, minimum password length, password age, and password lock-outs. The report also lists specific computers where password management is lacking.
Reports showing negative metrics can be used by IT professionals to convince the executives they work with to fund or approve more strict password policies. Reports that show high level of compliance compared with industry standards can be used to continually justify the effectiveness of the IT security team.

Network Detective Pro Updates
Data Collection Just Got A Lot Easier With New Discovery Agents
In addition to our tried and true network, local and cloud data collectors, Network Detective Pro users now have the ability to deploy and remotely manage “Discovery Agents” on any device that is not directly connected to the network – including workgroup computers and work-from-home machines. The agents can be set to run a computer and security scan on any Windows , Linux and macOS device, and do not require a password.
The Discovery Agent for Network Detective Pro is a lightweight, streamlined option that can be configured and deployed individually or on a bulk basis. The scan files that are generated after each scan are passed to user sites via a secure connection, and will be automatically integrated into all reports for that site. Any number of Discovery Agents can be installed for a specific site. Discovery Agents can be run in concert with any other Network Detective Pro data collectors to customize IT Assessments.


Compliance Manager GRC Updates
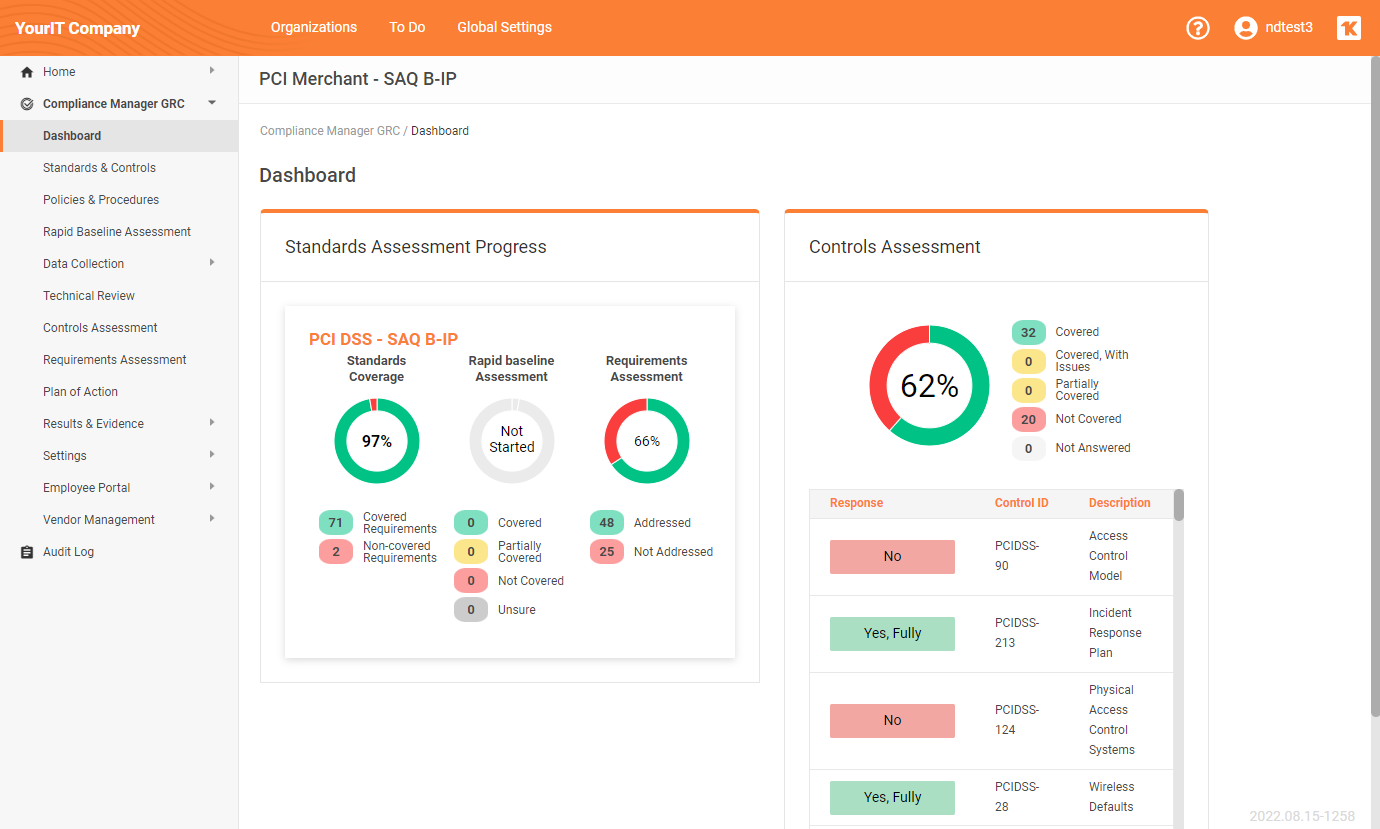
Get Into Compliance With PCI DSS the Easy Way
Compliance Manager GRC now automates and simplifies much of the PCI compliance process, letting you focus on what you do best.
If you, or your clients, accept payment cards to pay for goods or services – even if you completely outsource all cardholder data functions – you need to comply with the Payment Card Industry Data Security Standard (PCI DSS), a global standard that establishes everything you must do to protect credit card payment data.
Simply select the PCI DSS self-assessment questionnaire (SAQ) template that applies to your situation, and Compliance Manager pulls the right questions from the 1.800+ pages of documentation covering 300+ security controls covered by the standard.
You can run a Rapid Baseline Assessment manually to quickly see where you standand, and/or optionally run the built-in data collectors to answer some of the questions and provide evidence of compliance.
Then used the dynamic Plan of Actions & Milestones dashboard to address any issue and collect any missing information you’ll need to prove Due Care in the event of a breach.
You can also take advantage of the workflow integration with VulScan to meet the internal vulnerability scanning requirements.
VulScan Updates
Take Complete Control of Scanning with Custom Scan Profiles.
VulScan has released its latest feature upgrade with the addition of Custom Scan Profiles. VulScan previously offered three levels of scans (Low, Standard and Comprehensive) to users for them to identify vulnerabilities within the networks they manage. Now, we have bolstered that functionality and provided VulScan users the ability to leverage a fourth scanning option, which is the Custom Scan Profile.
Custom Scan Profiles allow users the flexibility to customize VulScan scanning tasks. For example, custom scan profiles can be created to target specific TCP and/or UDP ports or all of them at once. By utilizing this new functionality, users can perform low impact scans that only address those ports that are important. Also, users can now enter individual port numbers from lowest to highest or port ranges, with a dash between numbers, to easily define a custom range of ports to scan.
As always, this powerful new upgrade is available now to all VulScan subscribers at no additional cost.

Compliance Manager GRC Updates
New Consolidated Dashboard Gives You The Full Picture
We’ve created a new “consolidated” dashboard for you to view the progress of your assessments, regardless of the type of assessment being managed. Previously the different assessment types – Baseline Assessments, Standards Assessments and Requirements Assessments – each had their own “group” dashboards. These are still there if you want to continue to track the progress of all of one type of assessment you are doing together.
But our new consolidated dashboard shows the progress all of these different assessment types at the same time, and in the same place, grouped by standard. And a separate panel on the dashboard shows you the progress across all of the common controls.
This new view makes it much faster and easier to get the full picture of your overal compliance posture.
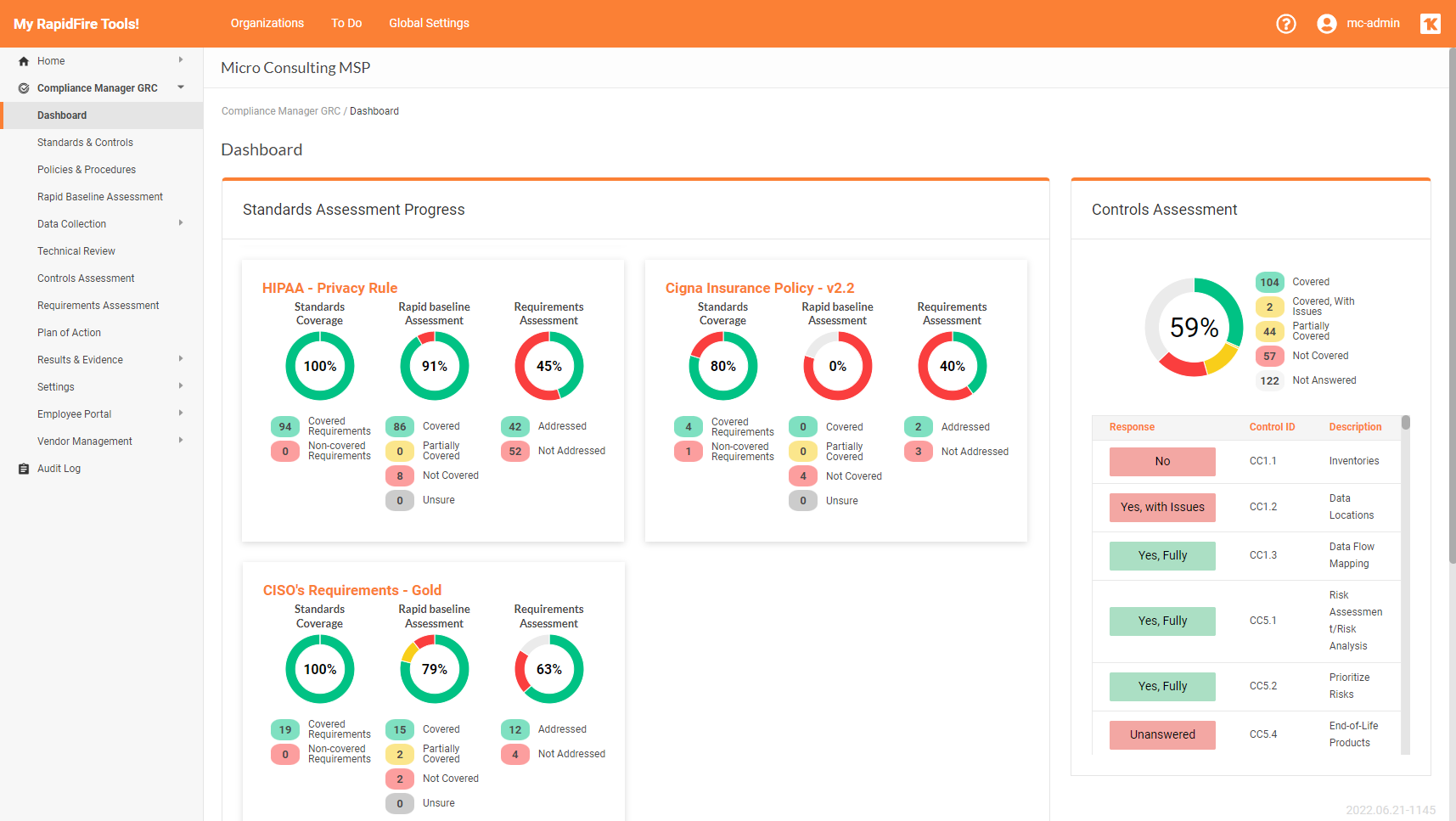
Enhanced Guided Survey Drives Improved Assessment Efficiency
We’ve updated the User Interface and added some nifty little hot keys to dramatically speed up the process of going through the Guided Assessment process.
As you go through the sometimes long-list of controls or requirements that you are assessing, instead of having to click on a radio button to chose your response and then hitting the next button to move to the next question, you now have the option to use keyboard hotkeys to select your response and optionally have the next question automatically pop.
This is especially useful when doing a Rapid Baseline Assessment when you are not taking the time to upload any files or adding comments. We’ve also rearranged some of the items on the screen to improve the overall experience.
Improve Communications With Vendor & Employee Dashboard Reports
You can now generate reports to show the same summary information that you see in the both the End-User and Vendor self-serve portals. You can also export the detailed data into Excel spreadsheets with the click of a button. This makes it easier to keep management aware of key employee and vendor governance and compliance progress.
The employee portal tracks which which employees have read and accepted whatever policy documents you upload for attestation. It also tracks compliance with whatever security awareness trainings you have assigned for them. More details about the status of individuals can be exported directly into Excel.
Meanwhile, Compliance Manager GRC includes a portal that you can provide to vendors who must prove to you compliance with specific requirements. You can track the progress of their compliance efforts through the portal dashboard, but you can also export the high level controls report as well as the detailed individual responses right into Excel.
This feature is particularly useful to share back with your vendors to stimulate them to attain compliance with the terms of your business agreements.
Network Detective Pro Updates
3 New Infographic Reports For Executive Consumption
We’ve just released three new infographic reports that IT professionals can give to the non-technical executives they report to, helping them to quickly report on key issues.
Network Detective Pro has historically been loaded with reports designed for IT professionals, helping to organize mountains of information into well-organized documents, and providing the technical details needed to identify and remediate issues and risks. But technicians often have a hard time generating reports designed for a non-technical audience to consume. These reports are designed for that purpose.
New Executive Summary Report
This is a new high level, highly-graphic report with dynamic elements that change based on the data feeding it. The report gives a high-level view of the health of different parts of the computing environment, including the network itself, hardward, software, security, passwords, and various Microsoft 365 cloud services, and color codes the categories based on conditions (from green to red). It also provides an overall issue/risk score (which can now be over-ridden or manually adjusted), as well as the total potential data breach liability value.
When the report shows one ore more of these categories “in the red,” the report can be used by IT professionals to start a conversation with the executives they work with to fund additional resources. Reports that show everything “green” help to show the continued effectiveness of the IT team and helps to keep that effectiveness top-of-mind.

New Data Breach Liability Summary Report
This new report goes beyond just the potential financial risk of a data breach, but also reports on the main causes of the risk. The financial risk is calculated based on the actual number of records discovered with sensitive data and the market-value of each record on the dark web. The report also includes the total count of records discovered with sensitive data, the number of missing critical patches, and the total number of computers with missing anti-virus/anti-spyware definitions.
In addition, a dynamic “risk meter” automatically adjusts based on the results of the other Key Risk Indicators shown in the report. Reports that demonstrate significant issues and liabilties can be used by IT professionals to convince the executives they work with to fund additional security programs. Reports that show low levels of risk can be used to continually justify the value of the IT security team.
The original, more detailed, Data Breach Liabilty report is still available in Network Detective Pro as back-up/supporting information, if needed.

New Password Policies Summary Report
IT technicians are asked to establish password policies to enhance computer security by encouraging users to employ strong passwords and use them properly. Password policies are also often part of an organization’s official regulations and may be taught as part of security awareness training.
However, IT professionals need a quick and easy way to report to executives password policy compliance to help enforce the policies. This report provides high-level metrics comparing end-user password behaviors to industry standard best practices. Among the metrics compared are use of historical passwords, minimum password length, password age, and password lock-outs. The report also lists specific computers where password management is lacking.
Reports showing negative metrics can be used by IT professionals to convince the executives they work with to fund or approve more strict password policies. Reports that show high level of compliance compared with industry standards can be used to continually justify the effectiveness of the IT security team.

Compliance Manager GRC Updates
Get BullPhish Training Content Inside Compliance Manager GRC
If you have subscriptions for both Compliance Manager GRC and BullPhish ID, now you can have the best of both worlds by creating evidence of compliance for all your security awareness training programs.
This integration brings 60+ different BullPhish ID security awareness training lessons, plus a validation quiz for each, right into the Compliance Manager GRC self-serve end-user portal. Multiple languages are supported.
You get the same kind of controls and reporting on the Bullphish training content that you get with the basic Security Awareness Training lesson included with Compliance Manager GRC:
- Assign specific training lessons to individuals and/or groups
- Notify end-users to log-into their branded Compliance Manager portals to access the training content
- Track who has completed viewing the content
- Record results of post-training validation quizzes
- Generate reports that can be used as evidence of compliance with training requirements.
With the combination of BullPhish ID and Compliance Manager GRC, you have the option to deliver end-user training directly from inside the Compliance Manager GRC self-serve portal, giving you bulletproof visibility into which employees are in compliance with their training requirements, and identify who needs to be called-out to meet their requirements.
Don’t have a subscription to Bullphish ID? Click here to learn more and get a demo.
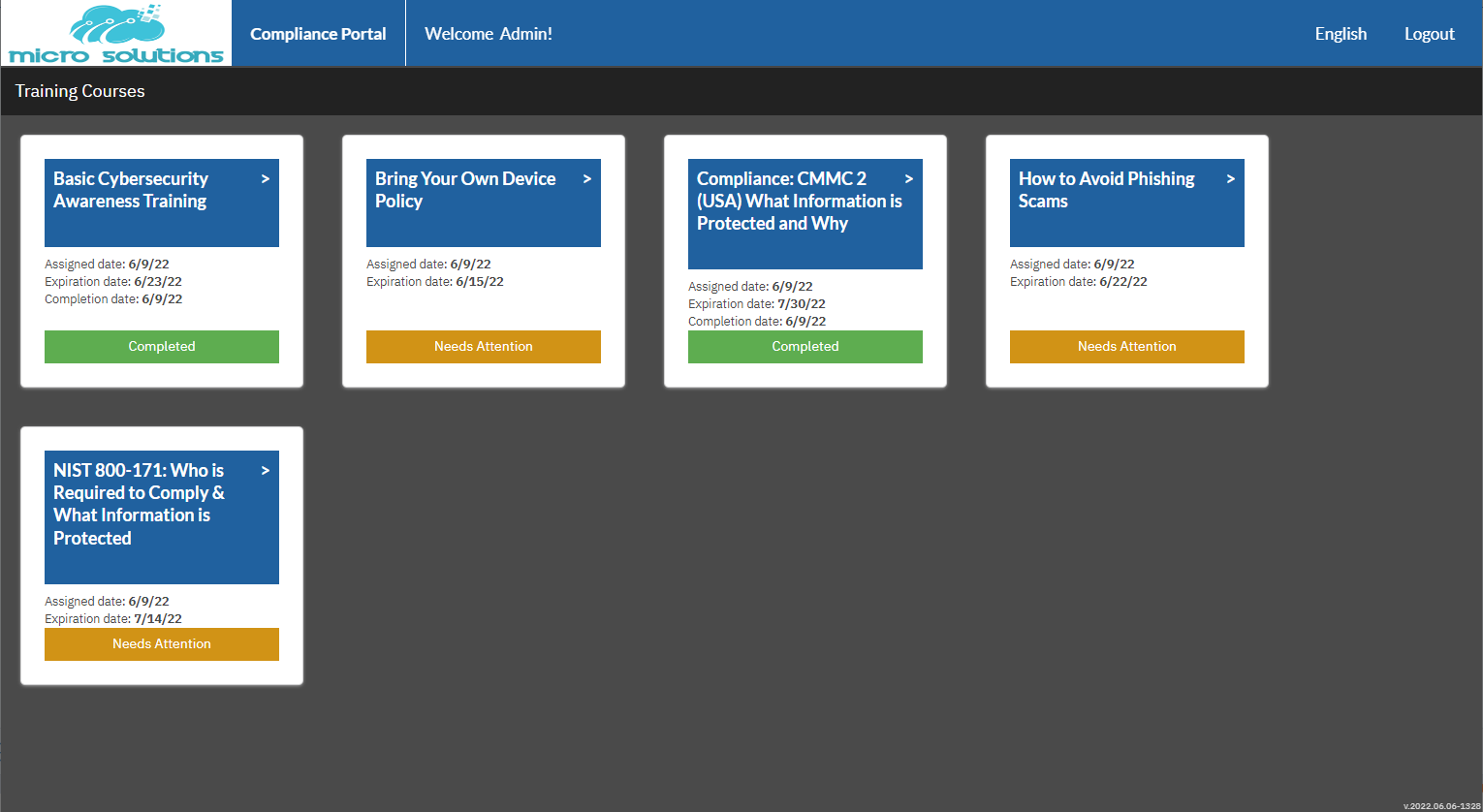
Automatically Generate Back-up Evidence of Compliance
Our latest integration allows you to pull data from the Unitrends back up logs into Compliance Manager GRC to generate evidence of compliance with the back-up requirements of any standards, including your own!
This integration automates the acquisition of data related to the last backup date for every device backed up using Unitrends, and then generates a Back Up Assurance Report – a critical document needed for any auditor. The report details the systems backed up and their current backup status.
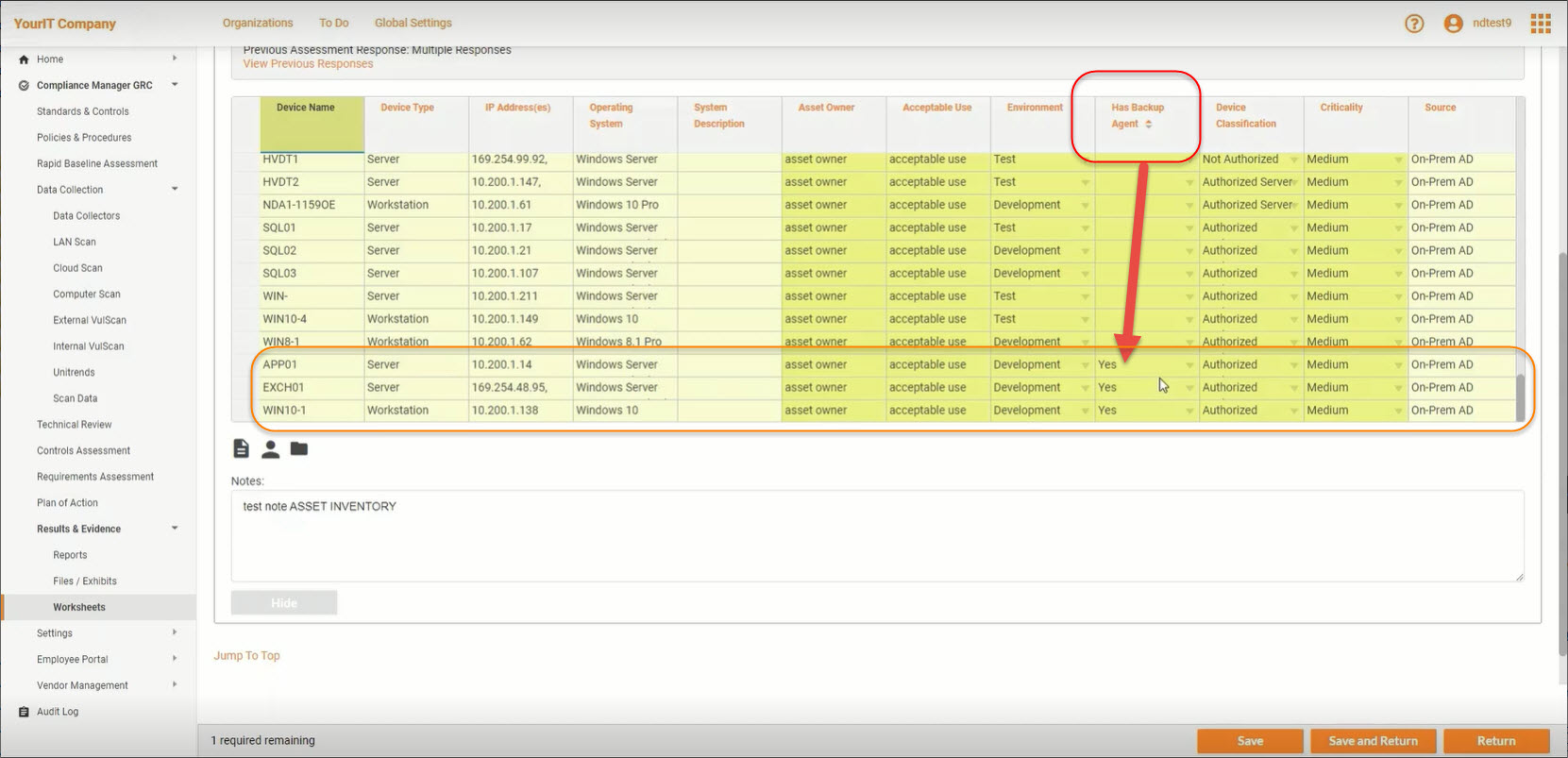
VulScan Updates
Harden Higher-Value Targets With Credentialed Scans
We’ve just taken VulScan to the next level by giving you the ability to perform Credentialed Scans on high value assets that may be prime targets for hackers.
Stardard vulnerability scans provide a quick view of vulnerabilities by looking at network services exposed by the host. Credentialed scans are set up by adding to VulScan the specific account/log-in credentials necessary to access the target asset(s) to be scanned. When the scanner hits those assets, it can automatically “log-in” using its stored credentials to do a more thorough check looking for problems that can not be seen from the network.
Credentialed scans are set up as separate scan tasks and can be run on an ad hoc basis or scheduled. The powerful new upgrade is available now to all VulScan subscribers at no additional cost.
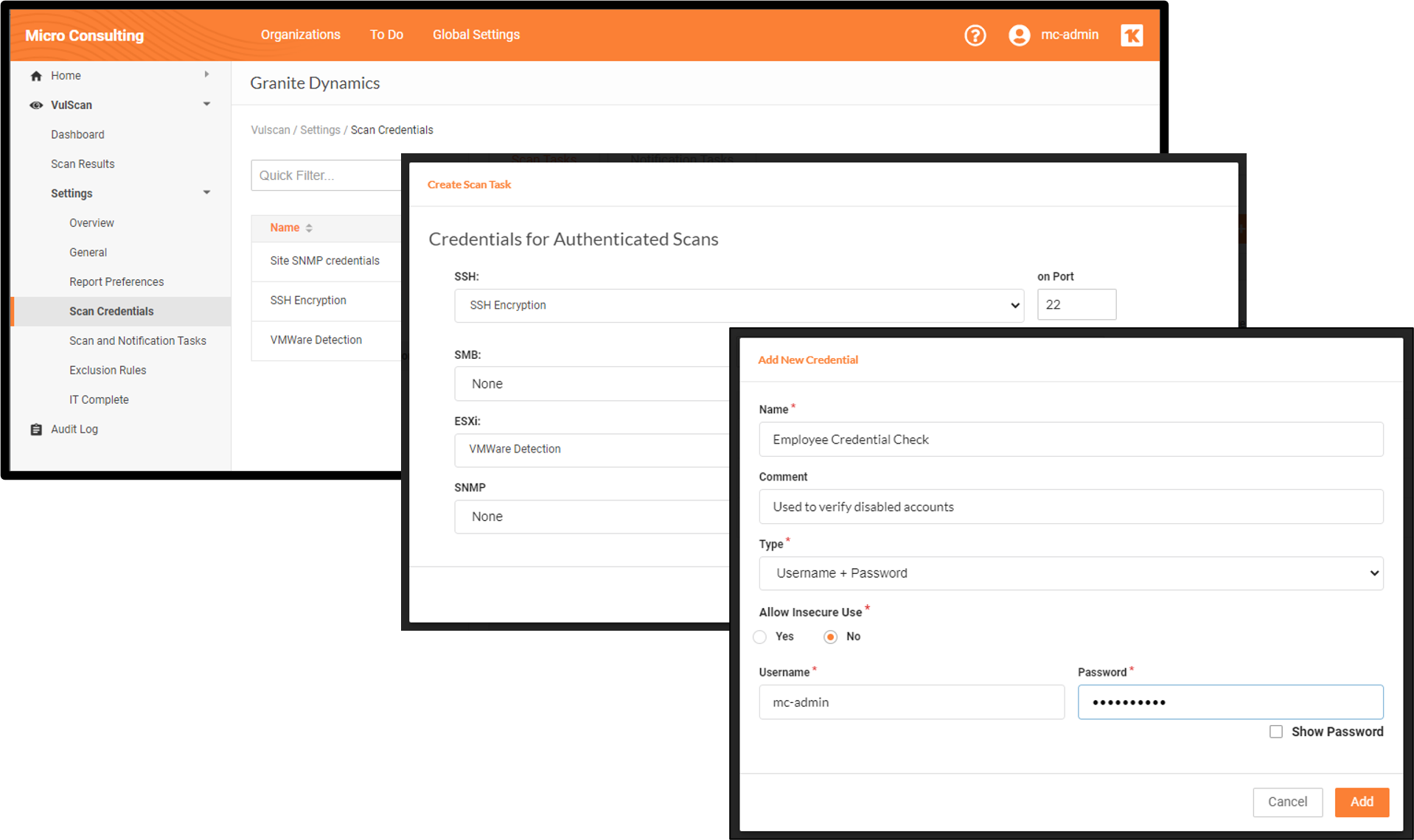
Compliance Manager GRC Updates
Cyber Essentials (UK) and Essentials 8 (AU) Standards Now Included
Great news for our users in the UK and Australia! We’ve added two new compliance management templates in Compliance Manager GRC to cover the de facto cybersecurity standards in both of these regions.
Cyber Essentials is the UK’s de facto basic cybersecurity standard. Compliance Manager GRC can help prepare you for the “self-audit” questionnaire required for certification, and provide helpful evidence of compliance that your third-party assessor can use to expedite a Cyber Essentials Plus certification.
Essential 8 is the country-wide cybersecurity maturity model adopted by the The Australian Cybersecurity Centre (ACSC). There are three different levels, and you can measure yourself against any one or all three at the same time.
Both of these new standards available without additional charge, and you’ll find them when you create a new site inside of Compliance Manager.
To keep track of all our new standards, and what’s coming down the pike, visit the standards section of our new Compliance Manager GRC website here; https://www.compliancemanagergrc.com/standards/
Network Detective Pro Updates
“Wow” Your Audience with Graphically Enhanced Summary Reports
Network Detective Pro’s Infographic Summary Reports are now available in a second design template, giving you more options for sharing information with your respective stakeholders.
Here are the reports that are now available in the new design:
- Dark Web Infographic Report: Provide risk assessments of domains and email addresses that may have been compromised on the dark web.
- Outdated Malware Definitions Infographic: Deliver risk assessments of computers and servers running outdated security definitions.
- Outdated Operating System Infographic: Provide risk assessments of computers and servers running outdated operating systems.
- Network Assessment Server Aging Infographic: The age of hardware in your environment can directly affect performance. As hardware gets older, the risk of failure increases. This report analyzes the age of servers in the environment.
NOTE: These infographic summary reports are not available in older legacy versions of Network Detective modules. To get these reports, plus new Azure infrascturer scanning, ability to adjust risk scores, and more, ask your account manager about upgrading to Network Detective Pro. You may qualify for a credit for your existing subscriptions. Stay tuned for more infographic summary reports coming soon!


Compliance Manager GRC Updates
Improved Compliance Management Workflow
Compliance Manager GRC now has an extra layer of automation to bring all responses and content input during a Rapid Baseline Assessment into the corresponding Controls Assessment for whatever scope is being worked. This streamlined workflow dramatically improves the efficiency of ramping up new compliance management programs.
With this update, all answers provided in the baseline assessment are translated into responses in the Controls Assessment. Any “Unsure” responses to the Baseline Assessment get translated as “no” on the Controls assessment until they can be validated. Any comments or supporting documents uploaded during the Baseline Assessment are automatically loaded into the Controls Assessment dashboard as well.
Next time you start a new assessment you’ll experience the joy!
Improved Visibility of Technical Issues
With this release you now have visibiltiy into specific technical issues that may impact the implementation of a given control that’s a part of your assessment. This was accomplished by updating the Controls Assessment User Interface within the Compliance Manager GRC dashboard to accomodate this valuable additional information.
We did the same for the Requirements Assessment. With this update, any responses provided in a Controls Assessment that may impact the requirements implementation are now referenced in the Requirements Assessment view in the Compliance Manager GRC dashboard.
Check it out!
Updated CMMC 2.0 Reports
New 800-171 Scoring Report for the Government Contracts
Complying with the federal government’s supply chain reporting requirements just got a ton easier.
Many federal government contracts, and all those for the Department of Defense, require contractors and subcontractors to provide the results of a self-assessment measuring their ability to protect what’s known as controlled unclassified information (CUI). To comply with this requirement, contractors must measure themselves against the requirements contained in NIST SP 800-171, and to score their assessment using a specific scoring methodology. This also applies to CMMC 2.0.
Compliance Manager GRC can now automatically generates a special assessment Scorecard Report from both the NIST 800-171 assessment template and the CMMC 2.0 Level 2 assessment. The report analyzes each individual response and deducts the specified points based on the government’s official scoring rules, and then provides the total score, which is required to be submitted to the official DoD Vendor Certification web site.
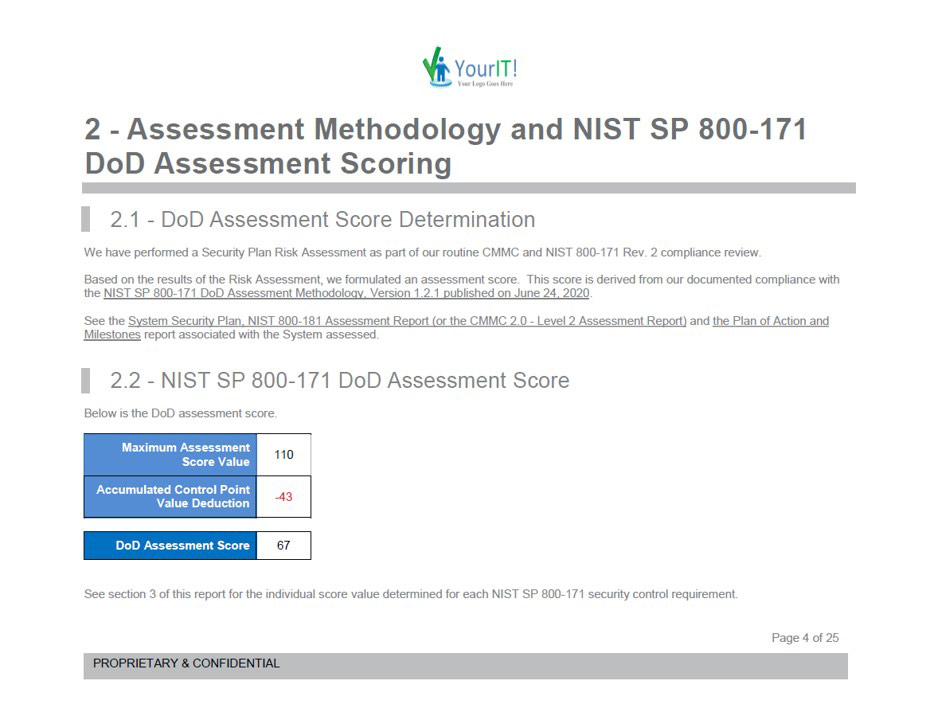
New System Security Plan (SSP) Now Included
In addition to submitting the scorecard results of the self-assessment, government contractors are also required to produce what’s called a “System Security Plan.” This is meant to be a comprehensive written document – or manual – that provides all of the details of how the organization meets all of the requirements of the NIST 800-171 standard.
Users of Compliance Manager GRC now get an incredible “bonus” report that can be generated with literally zero extra work. Upon the completion of either the NIST 800-171 assessment or the CMMC 2.0 Level 2 assessment, you can generate your fully-formatted and ready-to-submit SSP.
The time saved compared to manually generating these two documents from the ground up could easily cover your base subscription to Compliance Manager GRC for a full year!
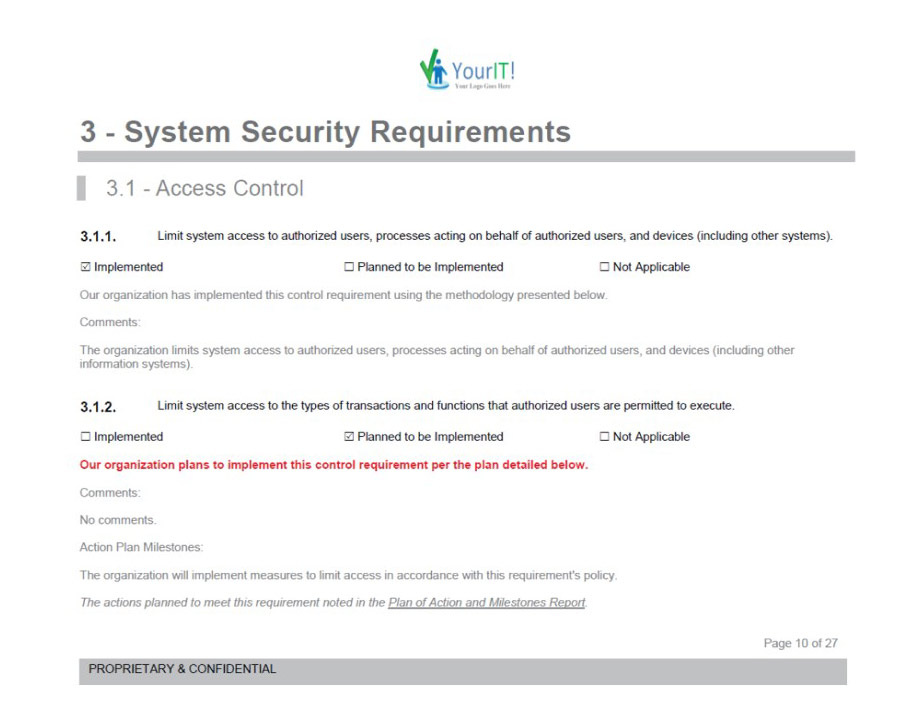
Network Detective Pro Updates
Customized Risk Scoring Now Available In All Reports
Many MSPs use Network Detective Pro to discover issues on prospect networks, and use the risk score to help pitch their services to win new customers.
Likewise, IT departments use the risk score in some reports to convince management of the need for additional resources.
However, for on-going reporting of network health, sometimes the built-in risk scoring algorithm in Network Detective Pro doesn’t reflect unique circumstances or exceptions that the IT technician is aware of.
That’s why we’ve added new controls to Network Detective Pro that exposes the risk score value associate with every issue, and gives the administator the ability to manually override the severity, score, and score value of every type of issue reported by Network Detective Pro.
This change gives you full control over how issues discovered by network scans are communicated in reports, saving time in editing reports and more accurately representing network health to clients (for MSPs), and managers (for IT departments).

Compliance Manager GRC Updates
Manage Vendor Risk with New “Self-Serve” Portal
Plenty of successful organizations rely on their vendors to provide them with quality goods or services that allow them to run their businesses.
But some government and industry regulations – like HIPAA and CMMC, for example – require that organizations also make sure that selected vendors are in compliance with the same IT requirements. And, even if regulations don’t require it, it’s always a good practice to make sure that any vendors who have access to your data.
Compliance Manager GRC now includes a “self-service” vendor risk management portal that makes it easy for third parties to complete assessments against any standards you pick, by logging into a branded web based portal and completing the appropriate questionnaires. You can optionally require the vendors to also upload their evidence of compliance.
Every Compliance Manager GRC site now supports the ability to “turn on” a Vendor Compliance Portal and provide log-ins to any number of vendors. This easy-to-use and manage portal allows organizations to more easily meet the vendor risk management requirements of any standard.
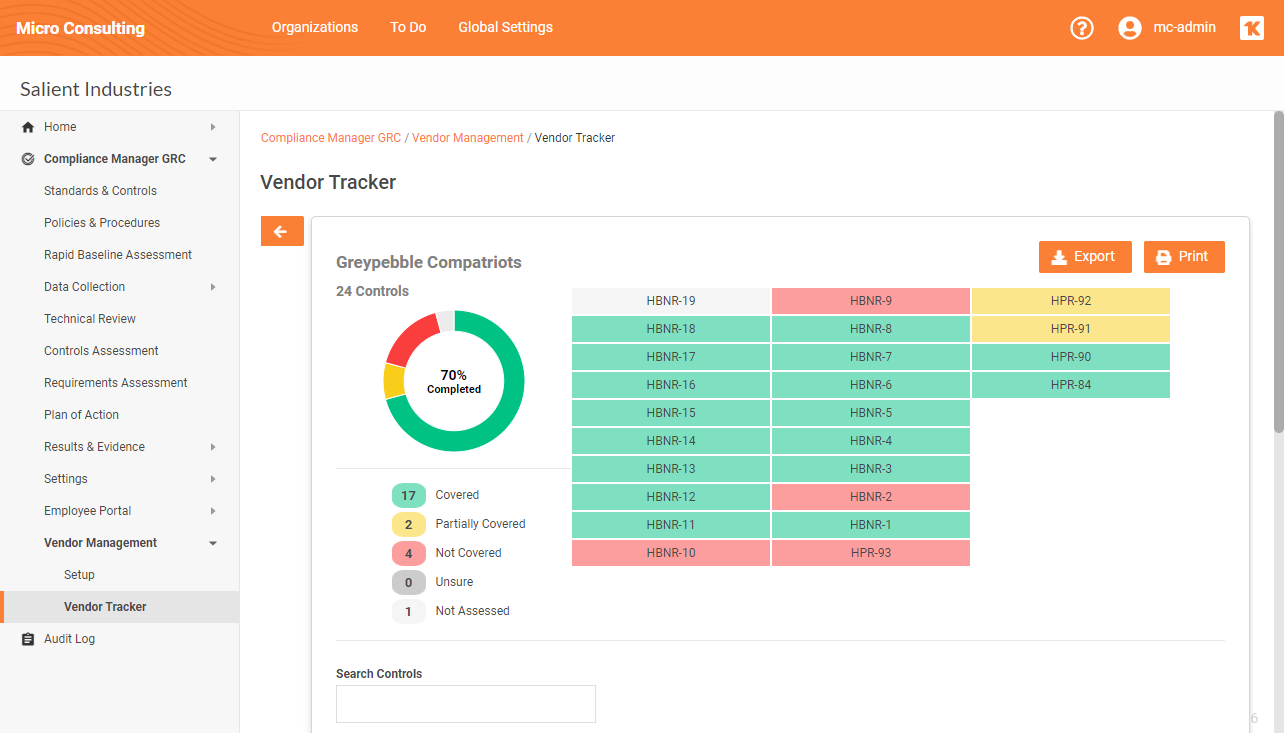
Compliance Manager GRC Updates
New Integration With IT Glue
Now you can have Compliance Manager GRC automatically send reports and documents into IT Glue for long-term storage, organization, and integration with reports and data from other sources. Files sent over to IT Glue are in MS Office format, allowing IT Glue users to store, preview and even edit documents within the IT Glue application.
The integration also allows the Compliance Manager GRC user to “pull in” documents that are stored in IT Glue, and “attach” them as evidence of compliance when performing compliance assessments for any standards, including custom standards you create.
IT Glue is quickly becoming the de facto choice of IT professionals for general storage and archiving of all their IT documentation, making this an incredibly valuable integration for users of both products.
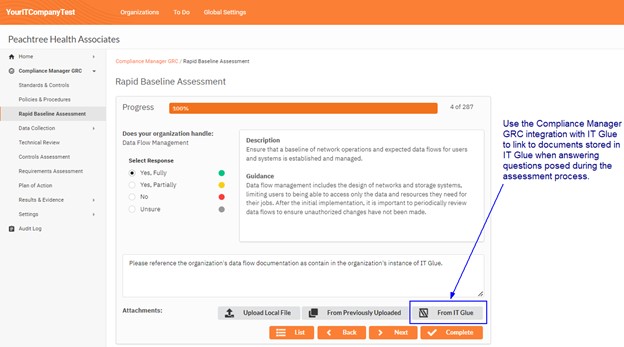
New End-User/Employee Compliance Portal Now Included
A critical part of most cybersecurity programs is tracking whether employees have read and acknowledged your policies, and whether they have taken your required cybersecurity awareness training. Every Compliance Manager GRC site now supports the ability to “turn on” a branded Employee/End User Self-Serve Portal to help meet these common compliance requirements.
Once set up, each employee or end user can obtain unique log-in credentials to access their own personal compliance dashboard. The dashboard includes a universal Security Awareness Training Module built right in, which can be set up as a requirement for each user. The user can take the course – which consists of a series of on-demand videos and post-training exam – and the system records the completion of the course and passing of the exam. Reports can be generated for compliance purposes.
In addition to the Security Awareness Training Course, the system allows the administrative user to upload any documents or policies that the organization requires employees to read and attest to the fact that they agree with the content of the document. The system records the “acceptance” of each document by each user, and reports can be generated for compliance purposes.
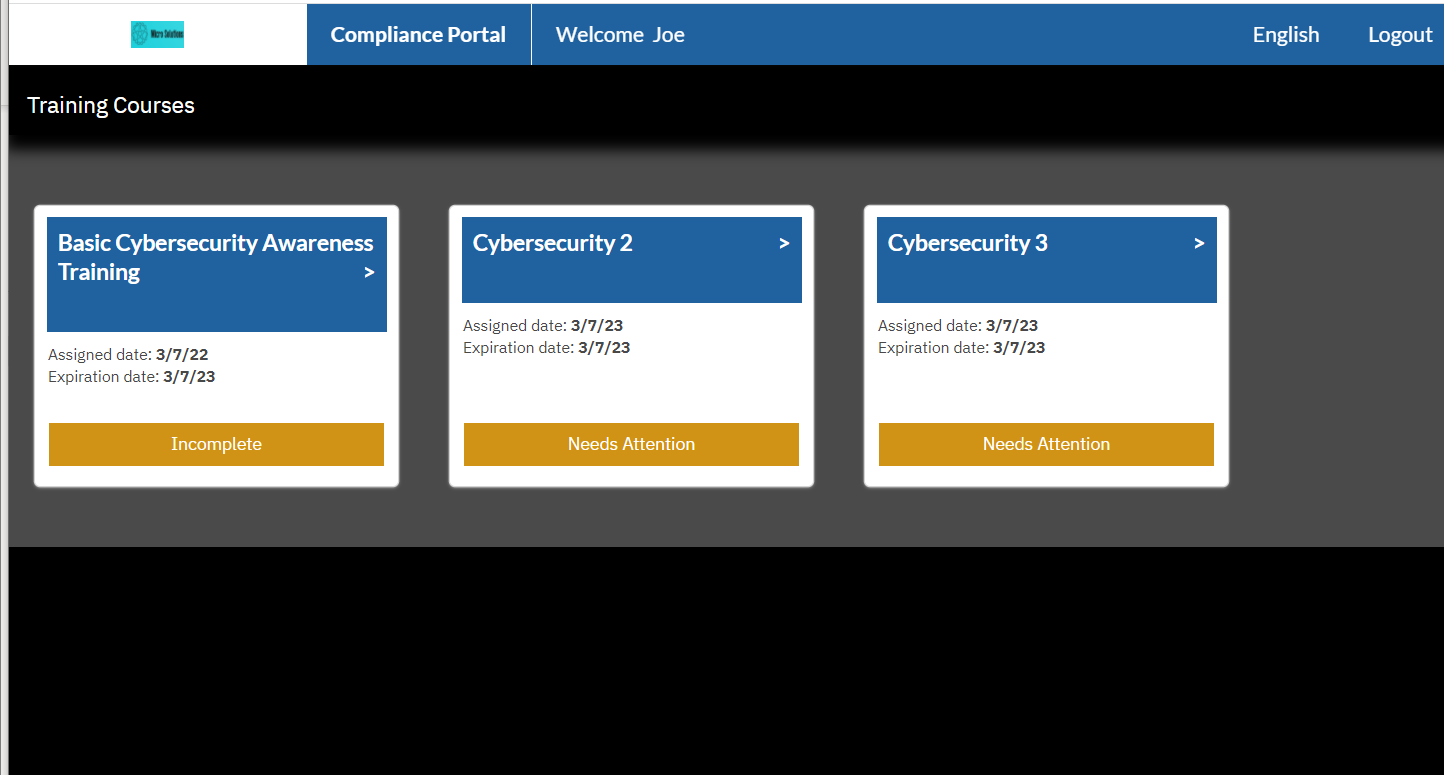
New Cyber Liability Readiness Standard Covers All Policies –
Compliance Manager GRC now includes a new specially-designed to help organizations prepare to submit Cyber Insurance applications, as well as to maintain compliance with the policy terms to be sure they are paid in the event of a claim.
The new standard is comprised of a superset of the most common cybersecurity requirements included in a majority of Cyber Risk Insurance policies. Adhering to the requirements of this standard should more than cover what is the minimum requirements of most policies.
MSPs and IT department staff also have an option to customize this standard to be a direct one-to-one match with the exact requirements of their own specific cyber risk policy. They can easily do this by cloning the Cyber Liability Readiness Standard, and then delete any controls or requirements that are not referenced in their application, or add any unique controls or requirements that the insurance company is asking for in their application.
Cyber-insurance is a specialty insurance product intended to protect businesses from Internet-based risks, and more generally from risks relating to information technology infrastructure and activities. Compliance Manager GRC is the first software solution that allows cyber-insurance policyholders to systematically document and provide evidence that they are meeting compliance standards.
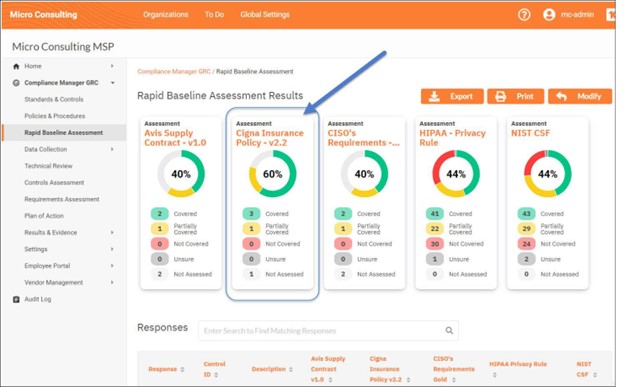
New Standard Covering All Banks, Insurance Companies and Financial Services Firms in NY
The New York State Codes, Rules and Regulations has some very specific IT requirements that cover thousands of organizations based in that state, as well as some of the companies that do business with them. The law and requirements are buried in Title 23– Financial Services – Part 500 – Cybersecurity Requirements for Financial Services Companies. The regulation is commonly referred to as NYDFS Part 500 (NYDSF stands for New York Department of Financial Services, the agency that oversees the regulation.
Under the regulation, every entity that requires a license from NYDSF – and their third-party service providers – must be in compliant with all of the cybersecurity requirements of Part 500. This includes:
- State-chartered banks
- Licensed lenders
- Private bankers
- Foreign banks licensed to operate in New York
- Mortgage companies
- Insurance companies
- Service providers
Every year they must file an attestation with the agency certifying that they are in compliant. These organizations also must create and maintain evidence of compliance for at least three years.
The good news for MSPs IT Departments within these organizations, is that Compliance Manager GRC now includes a built-in compliance management template specifically for NYDFS Part 500, with all of the requirements and associated controls built in so that you can do a Rapid Baseline Assessment in less than an hour. And, you can load up the DFS standard right along side any other standards you are following to manage all IT requirements at the same time from the same place.
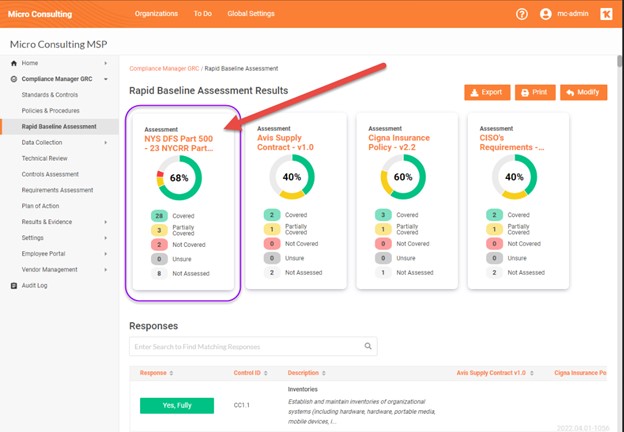
VulScan Updates
New Reporting Feature Meets Many Documentation Needs
VulScan now includes two new reports that you can generate directly from the Scan Results screen in the web-based portal. This powerful report generator allows you to filter the scan results that are displayed in the report, with options to choose which assets and issues are included based on the current filter.
The new feature includes a Summary Report by Issue, which rolls up all filtered issues together, and a Detail Report by Device, which show all filtered issues found per device.
Being able to generate these reports out of VulScan is important for MSPs and IT workers who need a quick and easy way to generate brandable and editable documents in MS Word format. Use case examples include:
- Generating reports for customers to prove scanning is being performed on their network,
- Generating reports for an auditor to show the latest scan results,
- Generating reports to be archived for compliance uses or for historical purposes.

New MAC Address and Hostname Groupings Improves False Positive Accuracy
This new feature enhances the entire VulScan system – from dashboard displays to False Positive Rules to Notification Rules – to allow you to identify and create rules for devices based on a MAC Address or Hostname. Previously only IP Addresses were exposed.
This improvement is particularly valuable in environments where the IP Address is not static, such as ones where DHCP (dynamic IP address) is used. If the same device is assigned a different IP addresses throughout time, a notification rule or false positive rule based on the IP address might be inappropriately applied to the wrong device. With this enhancement, you can now select the MAC Address or hostname to be used so that rules can be written that will work properly even in environments where IP addresses are not static.
NOTE: MAC Addresses are only available if scanning devices that are within the same subnet as the VulScan scanner.
Network Detective Pro Updates
Now You Can Export Your Network Detective Reports Into IT Glue
We’ve just completed a nifty workflow integration between Network Detective and IT Glue, which allows you to have selected Network Detective reports that you generate flow directly into the Documents area of IT Glue. This can be done automatically for reports generated by Network Detective’s Report Automation Server, or manually for ad hoc reports. Reports are uploaded as Office documents and can be previewed, edited, and downloaded directly from IT Glue.
This free workflow integration is available to customers who have both Network Detective and IT Glue, saving time in organization and retrieval of Network Detective reports and information.
Previously, options for storing Network Detective reports included saving to a local directory, network share or email. However, IT Glue is quickly becoming the choice of IT professionals for general storage of all their IT documents.
This integration also makes it easier for long-term archiving purposes and makes it easier for technicians in various locations to access the latest sets of assessment reports.


New OS and Security Reports For Downstream Communications
IT professionals are always looking for ways to provide simplified and more visual summary reports to the executives they work with. We’ve just expanded the Network Detective Pro report set to include two new dynamic, and brandable, infographic reports:
- Outdated Operating System Infographic
- Outdated Spyware/Virus Definition Infographic
Both reports are designed to be self-contained so they can be individually produced and shared as stand-alone documents. But they can also be combined with other reports to illustrate potential weaknesses that should be addressed, and are useful in obtaining authorization for additional funds to remedy the issues either as a one-time project or ongoing security enhancement program.


Compliance Manager GRC Updates
Automation of 2 Key Compliance-Related Documents
Today we published “Release 2” of Compliance Manager GRC, the next generation of our award-winning IT security assurance and compliance platform. This release includes the ability to dynamically generate a Policies & Procedures Manual for any standard you are managing – including custom standards! It can now also automatically produce a Plan of Actions & Milestones document that helps you keep track of required remediation tasks necessary to get you into compliance.
More Accurate Polices & Procedures Manuals
The previous version of Compliance Manager included a “hard-coded” Policy & Procedure Manual for each of the standards included with the software. While these manuals were extremely valuable as “explars” of the required evidence of compliance, they did not alway reflect the specific procedures that an organization might follow to meet a required policy. In addition, there was no way to produce any kind of customized Policies & Procedures documentation.
With this latest release, Compliance Manager GRC dynamically builds you a customized policies and procedures manual for each standard you are managing, and the manual relects any adjustments that you make to the procedures you follow. In addition, anytime you take advantage of the custom standard creation feature of Compliance Manager GRC – for example, if you create a standard to manage your own internal IT security program – Compliance Manager GRC will create a customized manual to document it. In addition, any time you make a change to your process in Compliance Manager GRC – like adding a new requirement, or changing the procedures you follow – the Policies & Procedures Manuals are automatically updated the next time you generate them.
Keep Compliance Remediation Projects Moving, and Documented
Meanwhile, any time your assessments indicate that you are out of compliance with any of your standards, you can generate an interactive Plan of Actions & Milestones document to help you manage the remediation tasks. You can view the report in the dashboard, or download it as an Excel Workbook with separate tabs for “Technical Issues,” “Control Issues” and Standards Issues.
The system automatically populates the report with specifics of the issues, including the status, weakness, what machines are impacted, how the weakness was identified, and the target milestone, and more. It then leaves space for you to add in the responsible party for addressing it, resources needed, scheduled completion date, changes to the milestones, and final status.
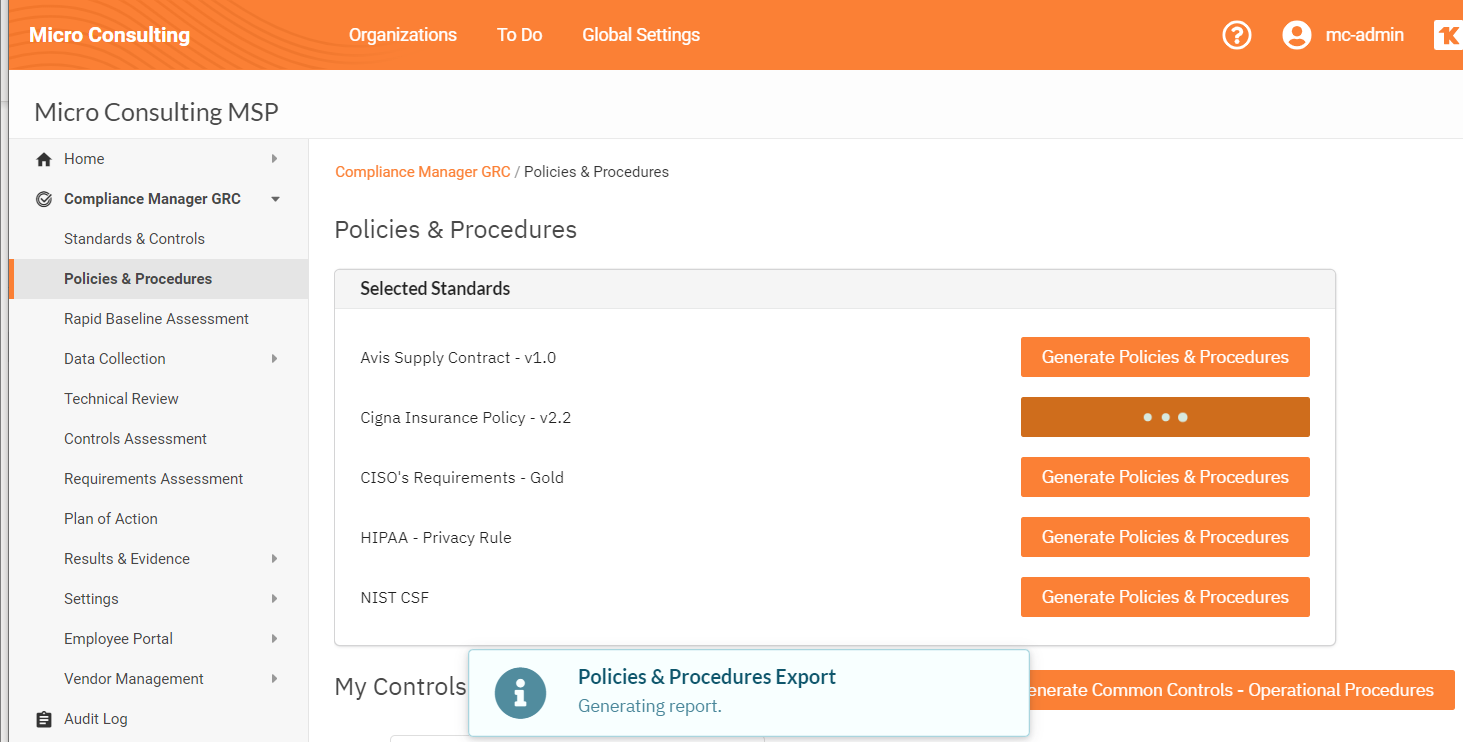
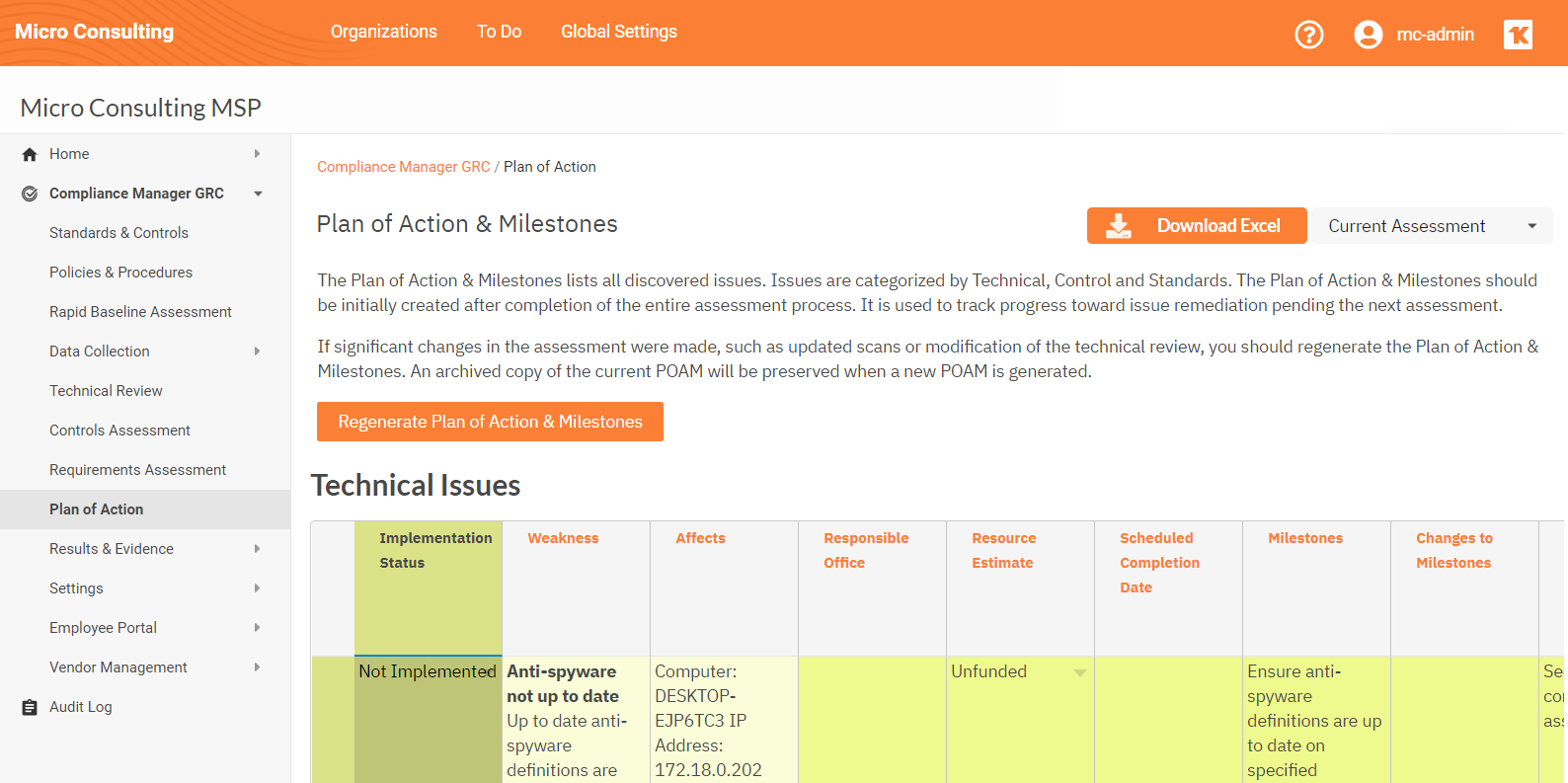
Compliance Manager Updates
Release 1 of Compliance Manager GRC
Today our development team published “Release 1” of Compliance Manager GRC, the next generation of our award-winning IT security assurance and compliance platform.
Release 1 includes a completely revamped compliance process architecture that is much easier to use, customizable for any security assurance and compliance requirements, and adds MS Cloud scanning – a much-requested feature. It allows IT professionals – whether they are MSPs or work in IT Departments – to quickly assess their level of compliance with whatever set of IT requirements they specify. The software includes a web-based dashboard that allows the IT professional to track and remediate compliance issues for multiple standards at the same time, dramatically reducing risk through improved and more efficient compliance management.
The initials GRC stand for the industry term Governance, Risk and Compliance. Security Assurance is a measure of confidence that the IT security systems meets its security requirements (defined by its policies and procedures) and is resilient against security vulnerabilities and failures.
Release 2 is coming right on the heels of this release. Look for it on or about March 9. It will include many new advanced features that moves Compliance Manager into the GRC and Security Assurance categories. We will update this column when Release 2 is out.

Network Detective Pro Updates
New Integration Reveals ACTIVE Passwords still on The Dark Web
Many tools that report on compromised passwords discovered on the Dark Web include when the password was compromised, but the reports can’t tell you if the password has been subsequently updated to address the risk.
A powerful new Network Detective Pro integration now analyzes the dates of compromise of passwords discovered by Dark Web ID scans, and compares them with the date of last password update captured by Network Detective Pro.
The results are automatically included in both the Network Detective Pro Full Detail Report, as well as in a new branded graphic for customers and prospects. Any compromised passwords that are active are highlighted in red in the full detail report.
Note: subscriptions for both Network Detective Pro and Dark Web ID are required to generate the new reports.


VulScan Updates
New Workflow Allows Ticket Creation From Issue Details
Our latest release includes an important new workflow innovation feature that gives VulScan users more granular control over the creation of service tickets from discovered network vulnerabilities.
With the click of a button, VulScan users can create individual service tickets inside of BMS (and other PSA solutions) directly from the Issue Detail screen within the web-based VulScan management portal.
Previously, the VulScan system could be configured to automatically create tickets of all discovered issues after each scan. With this latest enhancement, technicians have the opportunity to review and triage each issue before deciding whether to create a service ticket, mark the issue as a false positive, or ignore it.
Anytime a ticket is created in this manner, the issue detail screen will be updated with the ID# for the ticket that was created along with its status.
This latest workflow innovation provides significant improvements in remediation efficiency by eliminating the creation of tickets that don’t require any action.


Network Detective Pro Updates
New Control Added to Modify Risk Score Calculation
MSPs have been asking for more control over what issues are included in the calculation of the Risk Score that is included in several Network Detective Pro reports, including the Client Risk Report, Management Plan, Consolidated Report Card and others.
In this release we’re deliver a powerful new feature that allows Network Detective Pro users to configure the software to override any specific issues that they do not want to be factored into the proprietary risk scoring algorithms.
Network Detective Pro users can now access the complete list of all issue types through the preferences menu and de-select any issue they want to override from the scoring system. This action removes the issues from showing up on all reports that have scoring chart, and adjusts the score itself. These preferences can be set up individually by site, or globally.
We are working on additional enhancements to this feature that will give users even more granular control over the score by enabling them to adjust the actual point value attributed to each issue type.
Note: this new feature is not available in legacy versions of Network Detective that were purchased as separate modules. Reach out to your account manager to upgrade to Network Detective Pro.

Agent-deployment of Data Collectors Further Automates IT Assessments
Yet another game-changer out of the RapidFire Tools labs! You can now deploy and run the Network Detective Pro Network, Security and local data collectors automatically using VSA agents.
This powerful integration — now available through the Connect IT Automation Exchange — eliminates the headaches associated with reconfiguring network security settings, and makes it much easier to perform assessments on Workgroup environment and work-from-home situations.
Enabling this VSA-Network Detective Pro integration is a one-time setup that just takes a few minutes for each client site. Just download the script from the Automation Exchange, import it into VSA, and follow the simple step-by-step instructions to set up the Network Data Collector as well as the Security and Local Data Collectors.
From there, let the automation take over. The agents will automatically run the scans on any schedule you set up. The agents will download the latest data collector prior to running it, and then send the results back to Network Detective Pro to be viewed (via Data Explorer) or automatically output into reports or the Indoc Portal (using the Report Automation Server). The agent will even “clean up after itself” by removing any files it created during the process . . . including the scan files themselves.
If you have the combination of Network Detective Pro and VSA, recurring IT assessments for every client site have just become a reality!

Compliance Manager Updates
New UK-GDPR Module Released For Compliance Manager
Summary:
RapidFire Tools announces the addition of a new Compliance Manager module to cover the new UK version of GDPR, the data privacy and security standard first implemented in the EU several years ago. The new module is included as part of the base Compliance Manager Compliance Process Automation platform for MSPs and IT Pros managing network environments.
New Feature Description:
This new module contains all the same features and functions included in the EU-GDPR module, and adds the following:
- UK GDPR Compliance Questionnaire – replaces the original EU GDPR Compliance Questionnaire and includes Child Consent and forms for orgs outside the UK
- Show Guidance Functionality – The “Show Guidance” functionality with recommendations provided by the UK Information Commissioners Office (ICO)
- New Policies and Procedures documents have updated references to the UK GDPR
- Compliance “Issues/Risks” are now reported referencing UK GDPR “Articles”
Target Users:
The UK-GDPR requirement applies to every MSP and SMB organization within the UK. However, it also applies to any other MSP or IT Department located anywhere else in the world if they target, process, or store personal information of any UK resident. Even companies that are already compliant with the EU-version of GDPR will need to perform a separate UK-GDPR if they are accessing data on UK residents.
VulScan Updates
New “Portable” Scanner Add-on For VulScan
Some great news for MSPs and IT professionals who already have the VulScan network vulnerability management platform, and for everyone else in charge of securing the networks you manage.
Coming on the heels of our exciting launch of VulScan — which is designed for recurring vulnerability scanning of target networks, we’ve just released VulScan PVS, a “portable” vulnerability scanner that can be physically moved from one network to another for one-time or ad hoc scans.
To adequately protect the networks you manage, under normal circumstances you will want to perform both internal and external vulnerability scans on a regular basis on every device on the network. Best practices range from quarterly scans down to monthly, weekly, even continuous scanning, depending on the nature of the organization and type of data being collected and/or stored.
But sometimes, there are circumstances that call for an ad hoc or one-time vulnerability assessment when you wouldn’t want to permanently install a scanning appliance on the network. That’s where VulScan PVS comes in.
Use Cases For MSPs
- Ad-hoc vulnerability scans for prospecting
- Vulnerability scanning as part of one-time paid security assessments
- Annual scanning for insurance and other security compliance requirements
Use Cases For Internal IT Pros
- Vulnerability scanning for temporary offices
- Rotation among many smaller locations that do not require continuously recurring scans
- Ad hoc scans after major network changes
Contact your account manager for more information.
Network Detective Pro Updates
Now In BETA: MS Cloud Assessment Expanded . . . and Automated!
This one’s a real game-changer for Network Detective Pro users. Not only have we expanded the scope of the MS Cloud assessment to include more details about the Azure infrastructure, we’ve also finally cracked the code to automate your entire MS Cloud Assessment on a regularly scheduled basis without manual intervention!
First let’s cover the expansion of the MS Cloud Assessment now in Beta Testing for Network Detective Pro subscribers. In the legacy version of Network Detective, the MS Cloud Assessment module was optimized for one-off prospecting purposes by MSPs. It requires a manual authentication step as part of the set-up process, and the assessment is limited to Azure AD, as well as the main cloud services that make up Microsoft 365, including SharePoint, Teams, OneDrive and pieces of Exchange.
But with this upgrade to Network Detective Pro, we’ve significantly expanded the scope of the assessment to include a broader scan that discovers more information about the Azure Infrastructure.
New Details On Azure Infrastructure.
In addition to automating the data collection and reporting process, the upgrade also collects a wealth of information about the details of the Azure Cloud infrastructure, including:
- Azure Collection
- Azure App Services
- Azure Cloud Services
- Azure Databases
- Azure Load Balancers
- Azure Resource Groups
- Azure SQL Servers
- Azure Subscriptions
New Details On Virtual Machines
In addition to the major Azure infrastructure components, the upgraded Cloud Assessment also collects important details about each Azure virtual machine, including:
- Computer Name & Type
- Location & Status
- Operating System
- Virtual CPUs & RAM
- Host and Host Group
- Public IP Address
- Resource Group
- Subscription
New Automated Cloud Assessments.
The legacy stand-alone Network Detective MS Cloud Assessment module was optimized for MSPs to perform one-off prospecting assessments. It requires a manual authentication step as part of the set-up process, and the assessment is limited to Microsoft 365 and Azure AD.
The new MS Cloud Assessment upgrade in Network Detective Pro is designed to continue to add value for both MSPs and Internal IT Pros by allowing automated and recurring IT assessments on their recurring networks.
This is accomplished through the use of a simple Enterprise App that you create in your Azure environment that allows Network Detective to access the Azure environment via the Microsoft API without additional authentication.
Click here to access the Cloud Azure Scan Set Up Guide.
This upgrade is available now to all current Network Detective Pro subscribers only, and is not a feature included in the legacy Network Detective stand-alone Cloud Assessment Module. To enable the automation and expanded data collection, Network Detective Pro users simply install a special Enterprise App in the Azure environment talks directly to the Network Detective application to handle authentication.